
jirsak - stock.adobe.com
Citrix data exposed in third-party breach
Citrix CISO Fermin Serna said a third-party organization is investigating a data breach after some of the vendor's customer data ended up on a dark web marketplace.
A third-party breach may have exposed Citrix customer data on the dark web.
In a blog post Tuesday, Citrix CISO Fermin Serna confirmed reports that some of the vendor's data was on sale on a dark web marketplace. He said a third-party organization that held some of Citrix's data was investigating a breach, but that there is no evidence that Citrix was directly compromised.
"Last week a threat intelligence report circulated concerning claims made on the dark web by a threat actor alleging compromise of the Citrix network, exfiltration of data, and attempts to escalate privileges to launch a ransomware attack," Serna wrote in the blog. "Citrix continues to investigate those claims; however, we have no evidence that the threat actor compromised the Citrix network. Rather, all the evidence thus far indicates that the source of the data referenced in the intelligence report is a third party."
The threat intelligence report was shared confidentially with Citrix, and the vendor is not discussing the details publicly, a Citrix spokesperson said.
Serna said Citrix contacted the unnamed third party, which was "cooperative and responsive," and immediately isolated any Citrix-related data from the internet. "Once that action was complete, the author of the threat intelligence report reported that the threat actor's unauthorized access was terminated," he said.
The third-party organization, which is conducting its own investigation, was "only in possession of low sensitivity business contact information," Serna said. He added that any reports or claims on the dark web about Citrix source code, intellectual property and credentials being exposed are inaccurate.
Citrix declined to identify the third party. Serna said Citrix will assist the organization with its investigation and ensure "all appropriate disclosures are made."
It's unclear who wrote the original threat intelligence report that was circulated within Citrix last week, but chatter on social media about a possible breach began to emerge earlier this week. On Monday, an anonymous security researcher known as "Under the Breach" posted screenshots taken from the Russian-language website where a threats actor offered a "one-time dump of the customer base of a large company (USA)."
"Actor claiming he hacked Citrix.com and is now selling a database containing information on 2,000,000 users. Asking price: $20,000," the researcher tweeted.
According to Alon Gal, CTO of cybersecurity startup Hudson Rock, the data posted on the Russian cybercrime forum xxs.is and appeared to be legitimate.
"It's our assessment that the data, which was found on SQL server, appears to contain real and verifiable information on individuals that use Citrix," Gal said. "The hacker used a new account for this specific sale, which is a common thing to do in order to avoid leaving a trail behind."
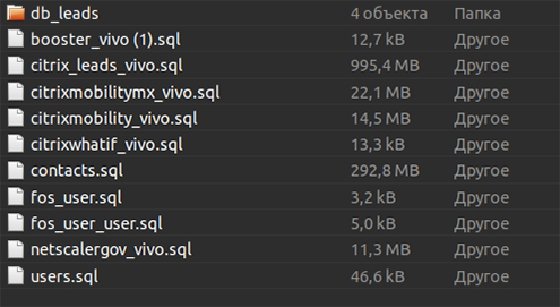
Gal provided a screenshot of the database the threat actor claims to have stolen.
"Notice 'NetscalerGov_vivo.sql'. We can only guess it possibly contains information about government contractors," Gal said.
Last year, Citrix disclosed a data breach after the FBI alerted the vendor that it had reason to believe threat actors had compromised its network. Following an investigation that lasted nearly five months, Citrix revealed cybercriminals did not access any customer data but did steal business documents. According to Citrix president and CEO David Henshall, malicious actors accessed the company's internal network via a password spraying attack that exploited weak passwords.





