
sudok1 - stock.adobe.com
FBI, CISA warn of impending ransomware attacks on hospitals
Trickbot and Ryuk ransomware actors are targeting hospitals and other healthcare providers, according to a joint cybersecurity advisory from the CISA and the FBI.
Hospitals are once again under attack by ransomware gangs.
Ryuk ransomware actors are targeting the healthcare and public health (HPH) sector, including hospitals and other healthcare providers, according to a joint cybersecurity advisory Wednesday night from the Cybersecurity and Infrastructure Security Agency (CISA), the FBI, and the Department of Health and Human Services (HHS).
After targeting systems with Trickbot malware, threat actors are deploying Ryuk ransomware against institutions including hospitals. Several hospitals have reported outages and ransomware attacks in recent days, though it's unclear if these incidents are Ryuk-related. For example, Sky Lakes Medical Center in Klamath Falls, Oregon, said in a statement that it was hit by a ransomware attack on Wednesday.
The advisory also warned of a new Trickbot module called "Anchor," which uses DNS tunneling to covertly transmit data and communications.
"In early 2019, the FBI began to observe new Trickbot modules named Anchor, which cyber actors typically used in attacks targeting high-profile victims -- such as large corporations. These attacks often involved data exfiltration from networks and point-of-sale devices," the advisory reads. "As part of the new Anchor toolset, Trickbot developers created Anchor_DNS, a tool for sending and receiving data from victim machines using Domain Name System (DNS) tunneling."
The advisory added that "Anchor_DNS is a backdoor that allows victim machines to communicate with command and control (C2) servers over DNS to evade typical network defense products and make their malicious communications blend in with legitimate DNS traffic."
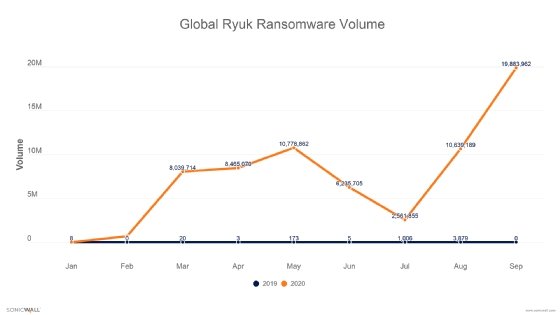
New research from SonicWall showed an extreme increase in Ryuk attacks. The company detected 5,277 Ryuk attacks through the third quarter of 2019, and 67.3 million Ryuk attacks through Q3 2020. The increase is so severe (a 1,275,245% increase) that a chart comparing 2019 Ryuk volume to 2020 shows a virtually straight line at the bottom of the graph. "Unfortunately, we've also seen an increase in attacks on hospitals -- and the problem may soon get much worse," the post said, citing Wednesday's alert.
In an Oct. 28 blog post about multiple malware families, Mandiant said it observed Anchor infections being deployed, although did not specify if such infections hit hospitals or other healthcare providers. In addition, the company only specified that they had seen Conti and Maze ransomware deployment following Anchor -- not explicitly Ryuk.
Jeremy Kennelly, analysis manager for Mandiant Threat Intelligence, told SearchSecurity that the Anchor threat isn't limited to Trickbot attacks on hospitals. "It is important to note that Anchor should be considered a standalone backdoor and not a module, but it does have multiple notable functions that enable it to run stealthily," Kennelly said via email. "Notable functions employed by Anchor to remain undetected include communication over DNS, communication with command & control servers resolved via Emercoin .bazar domains, and the use of Alternate Data Streams to store data."
Dmitriy Ayrapetov, vice president of platform architecture at SonicWall, said the addition of Anchor to Trickbot is "absolutely not surprising."
"The attackers are effectively "upgrading" data exfiltration techniques by using a DNS protocol that must be allowed for normal network operation," Ayrapetov said in an email to SearchSecurity. "Since DNS is not used for carrying any data, just for looking up addresses, it's not scanned as it's not an attack vector. The attackers are tapping into a clever technique that can use DNS to carry data, knowing that the vast majority of organizations do not have the capability to block this tunneling or are not looking for it."
Ayrapetov said DNS tunneling detection and prevention are not ubiquitous features, though some advanced firewalls have such features. He said all organizations should immediately block DNS tunneling to prevent this kind of malware communication and data exfiltration.
Earlier this month, Trickbot was disrupted by a private sector coalition led by Microsoft, as well as a technical takedown reportedly conducted by U.S. Cyber Command in an effort to prevent ransomware attacks on local, state and city election infrastructure.
In addition to the usual recommended best practices, such as patching systems and checking configurations, the advisory offered specific advice for system admins dealing with indications of a Trickbot compromise.
"System administrators who have indicators of a Trickbot network compromise should immediately take steps to back up and secure sensitive or proprietary data. Trickbot infections may be indicators of an imminent ransomware attack; system administrators should take steps to secure network devices accordingly. Upon evidence of a Trickbot infection, review DNS logs and use the XOR key of 0xB9 to decode XOR encoded DNS requests to reveal the presence of Anchor_DNS, and maintain and provide relevant logs," it reads.
CISA director Chris Krebs tweeted a warning to go along with the advisory's posting last night.
"Healthcare and Public Health sector partners - shields up! Assume Ryuk is inside the house. Executives - be ready to activate business continuity and disaster recovery plans. IT sec teams - patch, MFA, check logs, make sure you have a good backup point," he said.
The advisory said the current Ryuk threat will be "particularly challenging" for healthcare organizations dealing with the COVID-19 pandemic. The impact of ransomware attacks on hospitals can be devastating, disrupting not only IT operations but medical systems that are critical for emergency care.






