
alswart - stock.adobe.com
FBI removes web shells from infected Exchange servers
The DOJ announced the FBI had successfully removed hundreds of web shells from computers impacted by ProxyLogon and related Exchange Server vulnerabilities.
The FBI deleted a high number of malicious web shells present on several Microsoft Exchange servers -- but without informing or receiving consent from the owners of those servers.
The U.S. Department of Justice (DOJ) announced a court-authorized effort by the FBI on Tuesday to remove hundreds of web shells from Microsoft Exchange servers vulnerable to the massively-exploited ProxyLogon and related vulnerabilities. Last month, Microsoft revealed that four zero-day vulnerabilities in the on-premises version of Microsoft Exchange server, including ProxyLogon, were under attack from a Chinese nation-state group known as Hafnium; Microsoft patched the flaws, but a variety of attacks continued to impact Exchange servers.
The DOJ called the web shell removal operation "successful" in a press release regarding the effort. According to the press release, the FBI "copied and removed" web shells, which gave threat actors backdoor access to Exchange severs, by accessing U.S.-based victim computers without first informing the owners of those systems. However, the FBI said it "is attempting to provide notice of the court-authorized operation to all owners or operators of the computers from which it removed the hacking group's web shells" via email to either the owners and operators themselves or their ISPs.
"Combatting cyber threats requires partnerships with private sector and government colleagues," said Acting U.S. Attorney Jennifer B. Lowery of the Southern District of Texas, according to the press release. "This court-authorized operation to copy and remove malicious web shells from hundreds of vulnerable computers shows our commitment to use any viable resource to fight cyber criminals. We will continue to do so in coordination with our partners and with the court to combat the threat until it is alleviated, and we can further protect our citizens from these malicious cyber-breaches."
Despite the operation's success, questions remain about the operation, which began on April 9 according to court documents. While the documents were heavily redacted and light on specifics, they say that the FBI identified the file paths and passwords for the relevant web shells and issued commands to delete them.
The documents don't explain how the FBI obtained this information, or who infiltrated these organizations; the DOJ said the operation targeted "one early hacking group's remaining web shells," but it did not specify whether the group was Hafnium or another threat actor. The court order gave the FBI permission "to access the relevant victim computers" for 14 days starting from April 9.
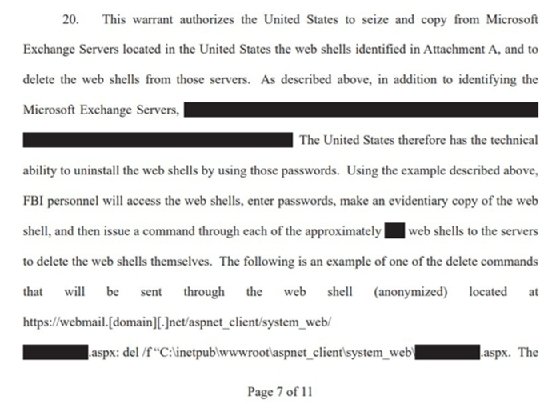
The affidavit for the court order said the web shells were installed prior to March 2, when Microsoft disclosed and patched the vulnerabilities. In other words, the specific attackers had gained access long before the operation, and the operation apparently did not include other threat actors or web shells implanted after Microsoft's March 2 disclosure.
According to an FBI special agent in the affidavit, whose name was redacted, they felt that remaining victims were unlikely to remove the web shells themselves.
"Based on my training and experience, most of these victims are unlikely to remove the remaining web shells because the web shells are difficult to find due to their unique file names and paths or because these victims lack the technical ability to remove them on their own," they wrote.
Microsoft declined SearchSecurity's request for comment. The FBI has not responded to SearchSecurity at press time.
While hundreds of web shells were removed, those removed don't represent the total scope of Exchange Server backdoors remaining in the country or world. On March 23, threat intelligence vendor Kryptos Logic said that it had found nearly 100,000 active web shells during ProxyLogon scans. The number of web shells remaining is unknown, but the danger for new Exchange server backdoors increased with the disclosure this week that four new remote code execution vulnerabilities had been discovered by the NSA.
Alexander Culafi is a writer, journalist and podcaster based in Boston.






