
ra2 studio - Fotolia
Researchers crack new Let's Encrypt validation feature
Multiperspective validation can be thwarted with a traffic-throttling technique that could lead to attackers obtaining digital certificates for domains they don't own.
A vulnerability in the way Let's Encrypt validates domain ownership could make it possible for cybercriminals to obtain digital certificates for domains they do not own.
The research team lead by Haya Shulman, director of the Cybersecurity Analytics and Defences department at the Fraunhofer Institute for Secure Information Technology, found that it is possible to thwart the certificate authority's (CA) multiperspective validation system when new certificates are issued for a domain.
Introduced in February 2020, Let's Encrypt's multiperspective validation was designed as a way to thwart hackers who use Border Gateway Protocol (BGP) hijacking to trick a CA into issuing valid security certificates for malicious or spoofed domains. By requiring a DNS host to answer multiple validation requests from different connections, it would no longer be possible to hijack a single BGP connection.
What Shulman and her team discovered, however, was that when these verification attempts to a nameserver fail, Let's Encrypt will exclude that server for a period of time. This leaves the door open to a downgrade attack.
By strategically throttling a number of different nameservers with a DNS provider, an attacker would be able to eliminate all of the nameservers but one. As a result, a compromised nameserver would be used to authenticate domain ownership.
"These techniques introduce packet loss in the queries between the nameserver and the validation authority," Shulman explained in a presentation at the Black Hat 2021 conference in Las Vegas. "It will cause the attacker to simply drop the query of the validation authorities."
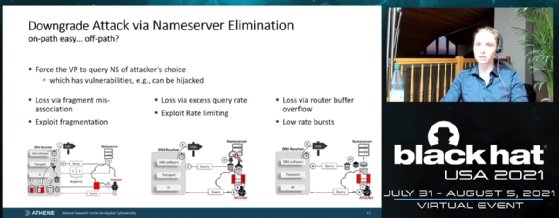
The technique is significant because it shows for the first time that not only can multiperspective validation be thwarted, but it can be done without the need for getting a man-in-the-middle condition through BGP hijacking. Shulman also said that because Let's Encrypt is the only CA using multiperspective validation, the attack technique could likely be modified to work with the DNS software for other authorities as well.
"We only needed to apply slight modifications according to the behavior of the DNS software at the CA," Shulman said. "Essentially, all the CAs are vulnerable."
The attack, Shulman noted, is not particularly easy to pull off, and for most domains it will probably not work; for example, the technique has not been tested on the open internet, as it would likely cause significant latency issues.
Still, the research team reckoned that approximately 10% of domains verified by Let's Encrypt, and around 11% of Alexa's top 1 million domains, would be vulnerable. Those would likely include numerous domains that would be popular targets for phishing attacks and other types of fraud.
To counter the attack, the research team recommended that Let's Encrypt and other CAs randomize the sources of the verification, which are cloud servers that perform the actual checks. This would prevent an attacker from knowing exactly what connections to bombard with traffic in order to pull off the downgrade attack.






