SolarWinds hackers Nobelium spotted using a new backdoor
Microsoft researchers believe Nobelium, the Russian-backed group that breached SolarWinds, has been using a backdoor tool called FoggyWeb since at least April.
The infamous threat group responsible for the SolarWinds supply chain attack are back at it with a new backdoor in its arsenal.
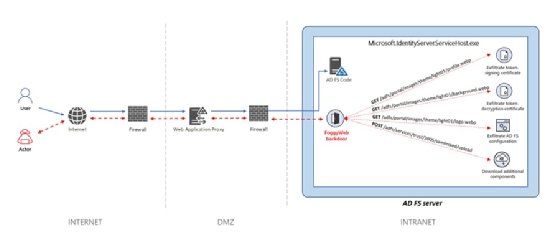
Researchers with the Microsoft Threat Intelligence Center believe the Nobelium crew is using a piece of remote access malware dubbed "FoggyWeb" to maintain persistence on compromised Active Directory servers. The backdoor had been observed in the wild as far back as April.
According to Microsoft researcher Ramin Nafisi, the FoggyWeb backdoor is used as part of the process of obtaining the user credentials that Nobelium hackers use to move across a network and access more valuable information. After compromising an Active Directory Federation Services (AD FS) server by way of bug exploits, FoggyWeb is then planted to give the hackers persistence on the server. From there, the credentials are remotely harvested.
The backdoor itself is encrypted within a loader application that is designed to disguise itself as a legitimate Windows DLL. Once loaded, FoggyWeb operates with administrator privileges.
"Once Nobelium obtains credentials and successfully compromises a server, the actor relies on that access to maintain persistence and deepen its infiltration using sophisticated malware and tools," Nafisi explained in the report.
"Nobelium uses FoggyWeb to remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificate, and token-decryption certificate, as well as to download and execute additional components."
Believed to be operating with the backing of the Russian government, Nobelium -- also referred to as Cozy Bear and APT29 -- is responsible for the 2020 hack of SolarWinds and numerous subsequent network breaches, thanks to a backdoor planted in Orion, SolarWinds' IT management platform.
Though SolarWinds was by far its largest hacking heist, Nobelium has operated for more than half a decade and has been involved in a number of other attacks, most notably the 2016 breach of the Democratic National Committee.
FoggyWeb is a different piece of malware than Sunburst, the backdoor deployed on SolarWinds' customer environments, and GoldMax, the remote access tool that the Nobelium crew used to get into SolarWinds' network. Nafisi explained that because the crew enjoys the backing of the Kremlin, it does not have to rely on off-the-shelf hacking tools and can, instead, build or, at least, source its own gear.
"We suspect that Nobelium can draw from significant operational resources often showcased in their campaigns, including custom-built malware and tools," he wrote in the report.
Nafisi provided indicators of compromise for FoggyWeb, mitigations for AD FS server configurations, and detections and hunting queries for security products such as Microsoft Defender for Endpoint, Microsoft 365 Defender and Azure Sentinel.







