Cybersecurity governance: A path to cyber maturity
Organizations need cybersecurity governance programs that make every employee aware of the cybersecurity mitigation efforts required to reduce cyber-risks.
In an increasingly challenging threat landscape, many organizations struggle with developing and implementing effective cybersecurity governance. The "Managing Cybersecurity Risk: A Crisis of Confidence" report by the CMMI Institute and ISACA stated: "While enterprise leaders recognize that mature cybersecurity is essential to thriving in today's digital economy, they often lack the insights and data to have peace of mind that their organizations are efficiently and effectively managing cyber risk."
Indeed, damages from cybercrime are projected to rise to $9.5 trillion globally in 2024, according to "Boardroom Cybersecurity Report 2023" from Cybersecurity Ventures. Consequently, board members and chief executives are now more focused than ever on cybersecurity, emphasizing the need to translate awareness into action.
How, then, can board leaders have confidence that their organizations are prepared for cyberattacks? The first order of business for most organizations is to enable a strong cybersecurity governance program.
What does cybersecurity governance mean and why is it important?
Cybersecurity governance, as per the ISO/IEC 27001 standard, pertains to the component of governance that addresses an organization's reliance on cyberspace in the face of adversaries. It involves directing and controlling security governance, specifying the accountability framework and providing oversight to ensure effective risk mitigation. This definition underscores the shift required from viewing cybersecurity solely as a technical or operational issue to recognizing it as an enterprise-wide risk management concern.
The U.S. Securities and Exchange Commission's new cybersecurity disclosure ruling, however, promises several positive impacts on cyber governance. Increased transparency through standardized disclosures might empower investors and incentivize companies to strengthen their defenses. Board-level focus on cybersecurity will drive more informed oversight. The standardized reporting also facilitates benchmarking and best-practice adoption across the industry. Finally, the emphasis on prompt incident disclosure encourages improved incident response plans and communication protocols. Overall, the ruling sets a higher bar for cybersecurity transparency and accountability, fostering a more secure and resilient organization.
With these factors in mind, the C-suite can then set the appropriate tone for the organization, which is the cornerstone of any good governance program. Establishing the right tone at the top is much more than a compliance exercise. It ensures everyone works according to plan as a team to deliver business goals and ensure the protection of assets within the context of a risk management program and security strategy.
Historically, cybersecurity efforts focused on implementing technical solutions to address specific problems or risks. Many cybersecurity departments have technical security safeguards, such as firewalls or intrusion detection, but they often lack basic cybersecurity governance policies, best practices and processes. Where they do exist, policies or processes are often outdated or ignored.
Many cybersecurity departments also have poor or inadequate cybersecurity awareness training programs that fail to address all levels of an organization. As shown by recent breaches, many organizations have inadequate hardening and patching programs. Poor access control practices, such as uncontrolled group passwords, shared accounts, proliferated admin privileges, shared root access and the absence of an authorization process, except at a low operational level, are problematic.
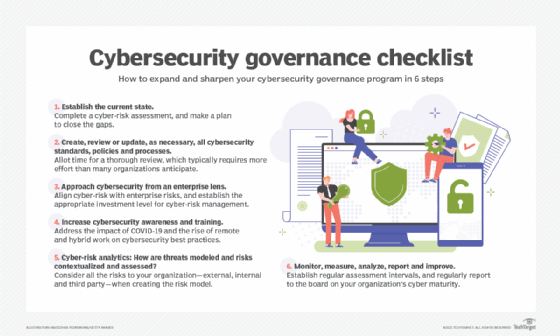
6 steps organizations should follow in their cybersecurity governance program
Here are six steps that can help an organization grow and sharpen its cybersecurity governance program:
- Establish the current state.
- Conduct a cyber-risk assessment and maturity assessment to gain a 360-degree view.
- Pinpoint vulnerabilities, evaluate existing controls and identify areas for improvement.
- Create, review and update all cybersecurity standards, policies and processes.
- Many describe this as low-hanging fruit -- and it is -- but it still is a heavy lift. Take the time needed to develop and establish the structure and expectations of cybersecurity governance.
- Implement well-defined cybersecurity policies, standards and procedures. This establishes a framework for managing risks and outlining roles, responsibilities and best practices for everyone in your organization.
- Approach cybersecurity from an enterprise-wide lens.
- Identify and prioritize critical data assets. Understand which information needs the strongest protection in alignment with business goals.
- Integrate cybersecurity as a strategic risk. Move beyond viewing it solely as a technical issue. Instead, embed it within your overall enterprise risk management framework.
- Align cybersecurity investments. Allocate resources strategically, considering the relative risks and potential impacts compared to other areas of investment.
- Increase cybersecurity awareness and training.
- With the rise in remote work and the ongoing adoption of hybrid work models, internal employees are no longer the only ones in need of training. Extend training beyond internal employees to encompass remote workers and their families. It is critical that the entire family understands good cyber hygiene.
- Assess cyber-risk analytics, and determine how threats are modeled and risks contextualized and assessed.
- When creating the risk model, consider all the risks to your organization -- external, internal and third party. Contextualize and assess risks comprehensively.
- Monitor, measure, analyze, report and improve.
- This is not a one-and-done exercise. Establish regular assessment intervals, measure what matters, analyze the data and create improvement plans.
- Report to the board on cyber maturity and the cyber-risk posture across the organization.
Security roles and responsibilities cross organizational boundaries
Leadership matters. Set a tone at the top that makes cybersecurity -- and cybersecurity governance -- a priority. But remember that leadership is not everything. Policies, standards and processes align cybersecurity governance with cybersecurity priorities so that cyber safeguards remain strong when leaders and employees change.
Remember, cybersecurity governance is a collaborative effort. Engage leadership, employees and stakeholders across all levels of your organization. By working together, you can build a resilient and secure environment that protects your critical assets, fosters trust and drives continued success.
Take the first step today. Invest in your cybersecurity governance program, and build a future of digital confidence.
Pamela (Pam) Nigro, CRMA, CISA, CGEIT, CRISC, CDPSE, serves as an ISACA board director and was the 2022-23 board chair. Nigro is vice president of security and security officer at Medecision, where she is responsible for all cybersecurity efforts that secure and protect information important to Medecision and its customers, while ensuring the overall cyber resiliency of the company. She is an experienced board member, recognized thought leader and subject matter expert. Nigro is also an adjunct professor at Lewis University in Illinois, where she teaches graduate-level courses on health information security, healthcare data security, privacy, confidentiality, healthcare informatics, ethics, risk, IT governance and compliance, and management of information systems in the MSIS and MBA programs. She has more than 25 years of experience in the healthcare industry and the IT industry and holds numerous IT certifications. Nigro achieved her MBA from Illinois Institute of Technology. She also achieved her "Distinguished Toastmaster" from Toastmasters International. She is an industry and keynote speaker and contributor to industry articles and journals, as well as industry certification review manuals and training materials.






