peshkova - Fotolia
Using virtual appliances for offload is a key encryption strategy
Using a virtual appliance to process traffic is a key encryption strategy enterprises can use to improve throughput. The results are striking
It is not uncommon for a corporate perimeter security strategy to be based on a series of appliances. Intrusion prevention devices, next-generation firewalls (NGFWs) and application firewalls are part and parcel of a multi-tier security perimeter. Deploying multiple physical devices, however, can be a logistical nightmare; as a consequence, security functions are good candidates for migration to virtual appliances (VA). But the convenience offered by virtualized security can also result in a drop in performance.
Traffic bottleneck complicates encryption strategy options
By definition, security devices inspect traffic and decide if the traffic (packets) should be forwarded or filtered (dropped). When incoming traffic arrives encrypted -- through Secure Sockets Layer or, more likely, Transport Layer Security -- it must first be decrypted before it can be inspected and re-encrypted as it is passed on.
Cryptographic functions are CPU-intensive. In a physical world, security devices could be engineered to offload the required processing by handing it off to a separate piece of hardware. A virtual appliance, by default, would use its own virtual CPU (vCPU) to handle both the cryptographic functions and its core packet inspection work. As a result, rather than inspecting traffic, a significant portion of the VA's vCPU could be consumed opening and reclosing the encryption envelope. Thus, effective security throughput would drop. This could ultimately degrade user experience or require additional VAs to be put in place to handle the load.
The answer is simple
Do what the original appliances did and offload encryption tasks to a virtualized security processor; that is, a specialized hardware module that is made available as a virtualized resource. This is a key encryption strategy and it allows the security VA to focus on inspecting traffic. It will also lead to improved throughput.
This capability is now available, at least in certain virtualization platforms. The Tolly Group -- a company I founded -- had the opportunity to benchmark one of them recently and put this theory to the test.
Determining effectiveness of the encryption strategy
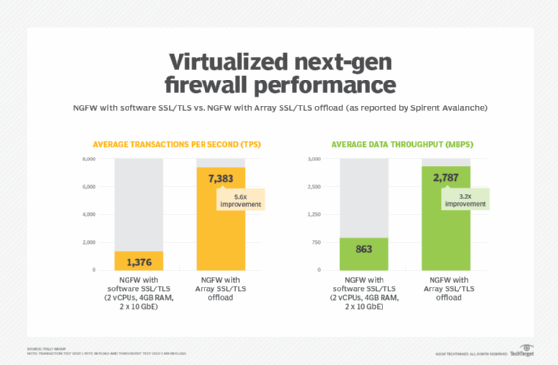
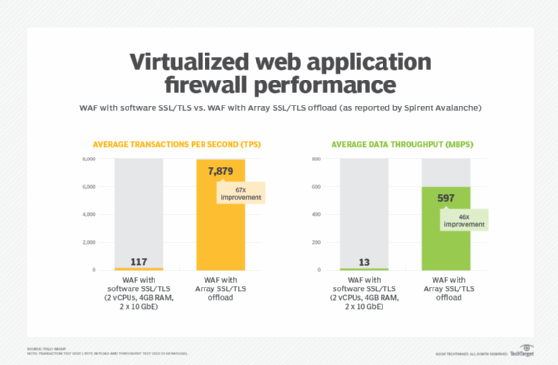
Proving the benefits of encryption offload for virtualized appliances is easy -- benchmark before and after. In our evaluation, we looked at two different security appliances: a web application firewall (WAF) and an NGFW offered by prominent security vendors.
Two benchmarks were used: transaction processing (using small payloads) and data throughput (using large payloads).
For the before scenario, a security VA handled all encryption on its own. For the after scenario, a decrypt virtual appliance -- linked to the hardware processor -- decrypted all inbound traffic and fed it to the security appliance. After processing, the security VA sent the data to an "encrypt" VA -- also linked to the hardware security processor. This VA encrypted the data traffic and forwarded it on. The results were as follows:
WAF: The results were impressive, especially for the WAF VA. (Web application firewalls need to inspect "deeper" than regular firewalls and, thus, have greater overhead.) Without encryption offload, the WAF was only able to process 117 transactions per second (TPS). Once traffic was unloaded, processing skyrocketed to 7,879 TPS. Data throughput also improved dramatically. Without the hardware assist, throughput measured 13 Mbps; employing the security offload boosted throughput to 597 Mbps, 46 times greater.
NGFW: Without the encryption offload, the NGFW processed 1,376 TPS. Adding the security hardware offload to the NGFW VA accelerated processing to 7,383 TPS, a more than 500% jump in performance. The amount of data transmitted, meantime, rose from 863 Mbps to 2,787 Mbps once security was offloaded to a dedicated VA.
The Tolly Group ran this test for Array Networks on its AVX Network Functions Platform. The full report is available here.