
alphaspirit - Fotolia
Becoming a cybersecurity professional: What are the options?
A cybersecurity professional has several options for their career path. Expert Ernie Hayden reviews the cybersecurity career track options and what skills are required for each one.
It is common knowledge in the global cybersecurity community that there is a multitude of unfilled cybersecurity jobs, and there will be even more in the coming years. Some statistics range from 1.8 million open jobs by 2020 to 3.5 million unfilled jobs by 2021, according to Cybersecurity Ventures. Both are very large numbers and, of course, the question remains, where will all these qualified candidates come from?
The question of how to fill these openings is its own matter, but there is a way to give cybersecurity candidates an opportunity to understand the cybersecurity profession and to help them get a sense of the different facets or realms of this vocation.
The Cybersecurity Profession Framework
A professional framework can be an important tool for cybersecurity professional career development; for example, the National Institute of Standards and Technology's NICE Cybersecurity Workforce Framework describes and categorizes work within the cybersecurity profession.
Another map of the job landscape came into being almost 15 years ago, when two Seattle-based CISOs began to build a framework of the cybersecurity profession. The concept began on a paper napkin at a small café and ultimately progressed to a formal structure and skeleton.
At a high level, this framework is intended to show the reader -- whether an experienced CISO or cybersecurity professional, or a new person exploring the idea of becoming a cybersecurity professional -- that there is a semblance of hierarchy and flow in the profession. This model can show the individual perusing the key aspects of the profession that there are many opportunities, from the frontline to the back office, and that every job has its tactical and strategic importance.
The higher level facets of the framework can be seen in the image below.
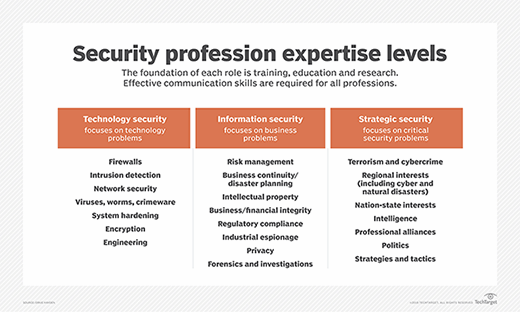
Technology security
Technology security tends to be the first area most individuals think of when considering a future in cybersecurity. Technology security normally includes such tools and devices as firewalls, intrusion detection systems, network security and architecture, antivirus/antimalware tools, system hardening techniques and processes, security engineering, encryption, and other cryptographic processes.
Daily work in this area is important and should be focused on the bits and bytes, as well as the ports and services aspects of network and system defense. This would be an excellent area for someone with keen attention to detail and the ability to mentally visualize security problems and the necessary solutions.
In summary, technology security includes the tactical, day-to-day, sword-and-shield aspects of being a cybersecurity professional.
There are excellent training resources for the new cybersecurity candidate to pursue as they enter this domain, including the CompTIA Security+, Network+ and Cloud+ certifications. Additionally, the basic SANS courses can provide an excellent foundation for new cybersecurity candidates entering the technology security area. Similarly, experience with elementary scripting/coding -- such as Ruby/Ruby on Rails, Java or Python -- is a great way to begin a technical cybersecurity career.
Information security
The second column of the model above includes the broader, programmatic aspects of cybersecurity. This domain is less focused on technology and more on data and information protection by means of programs, processes, policies, standards, procedures and guidelines. The predominant activities involved in this arena include risk management, governance, regulatory compliance, business continuity and disaster recovery, intellectual property, business/financial integrity, industrial espionage, privacy, forensics, and investigations.
These cybersecurity activities focus on protecting the business, protecting its data and ensuring the business is compliant with associated cybersecurity rules, regulations and guidance.
Generally, one can begin a career in this domain without knowledge or experience in the technology security pillar, but a strong start and knowledge of technology security will provide a cybersecurity professional with better tools to not only recognize weaknesses and vulnerabilities, but to have a better grasp on technical, as well as programmatic solutions to problems.
Certification in this area of expertise includes the Certified Information Systems Security Professional from ISC2 and the Certified Information Systems Manager from ISACA.
The last vertical of this model, strategic security, offers an excellent next step for cybersecurity professionals in their career progression.
Strategic security
The strategic security pillar is primarily an area of strategic importance to national cybersecurity interests, defense and warfare. The career players tend to be in the military, national intelligence agencies and strategic cyberthreat intelligence at a corporation or university. Each day involves solving strategic cybersecurity problems.
The areas of work within this pillar include cyberterrorism and physical terrorism, cybercrime, cyberwarfare, nation state and regional cyber interests, national and international cybersecurity doctrine and policy, threat intelligence and analysis, professional alliances, politics, strategies and tactics, and others.
Success in this domain requires strong skills and capabilities in strategic and big picture cybersecurity analysis. Understanding security and intelligence tradecraft is important, as is having a passion for geopolitics.
A great place to start building skills in strategic security is working with government intelligence agencies or the military.`
Foundations: Training, education and research
Each day, as you read the news, you hear about the needs -- and products -- offered by security training providers and research entities. Both of these could be starting points for cybersecurity professionals. At a minimum, a cybersecurity professional should be exposed to appropriate training and education activities. Also, simple employee security awareness courses and videos are an important aspect of a cybersecurity professional's career.
Cyber research is for the deeply experienced professional who enjoys and understands reverse-engineering of code and malware. Most of these successful researchers come up through the technical security ranks, usually starting at a young age. They are always inverting the equation and looking at security challenges in totally different ways.
That said, research is critically important to our profession. No matter what level of cybersecurity professional you are, be sure to follow and study the results of researchers such as IOActive, Sophos, Symantec, McAfee, F-Secure, etc. Also, pay attention to US-CERT, ICS-CERT, Idaho National Laboratory, and key university cyber research programs, such as the Carnegie Mellon CyLab.
The most important skill: Effective communications
The most important foundational skill cybersecurity professionals need is the ability to effectively communicate their ideas, messages and conclusions. This means you need to understand how to effectively use today's communications tools, such as Microsoft Word, PowerPoint and Excel.
You need to know how to write in complete sentences and organize your ideas and conclusions in a precise and succinct manner. You need to know how to prepare and give a speech or presentation to executive management, as well as to your fellow technicians. This takes focused practice and is incredibly important. You can be the smartest cybersecurity professional in the world, but if you cannot effectively and accurately communicate your ideas and conclusions, you will probably have a hard time succeeding in this field.
Therefore, you must study the technology, programs and processes, but be a skilled communicator, too.
Using the framework
There are no tried and true ways to use this cybersecurity profession framework. Some ways to use the framework include:
- Orienting students to understand the opportunities and possible career paths available for cybersecurity candidates.
- Giving cybersecurity professionals the sense that staying in a singular pillar -- such as the technology security column -- is an acceptable career path. The world needs strong and experienced firewall engineers, so there is no immediate need to simply get your qualification card checked before you move to another pillar.
- Providing an orientation of future management opportunities for each of the security pillars. Strong and knowledgeable managers and leaders are required for each pillar of the framework.
Essentially, this is just a framework, and it is still subject to interpretation and modification as our technologies and methodologies -- as well as our threats and cyber enemies -- evolve.
A final thought
A fun and interesting white paper offers some guidance to cybersecurity professionals, or cyber warriors, on career paths with different levels of experience. The white paper, entitled "Self-Development for Cyber Warriors," was written in 2011 by Gregory Conti, James Caroland, Thomas Cook and Howard Taylor.
It is a well-written essay on ways a person interested in cybersecurity can develop his knowledge through self-development and lifetime learning. This includes activities such as professional reading -- including science fiction; following technology news, security blogs and magazines; reading and studying journal articles from Foreign Affairs, Small Wars Journal, etc.; reading military field manuals; participating in local security meetings and associations; and attending regional, national and international cybersecurity conferences. The authors even recommend viewing selected videos and movies to gain added perspective on the challenges of cybersecurity.
Overall, the white paper is a worthwhile read for any level of cybersecurity professional and can be used as a checklist of development activities to help guide your cybersecurity knowledge and experience growth.








