Benefits of virtual SOCs: Enterprise-run vs. fully managed
A virtual security operations center, be it managed in-house or by a third party, is becoming an increasingly popular option to save money and improve reliability.
The security operations center has evolved to meet current enterprise demands. Multiple SOC options exist today that may meet your organization's needs. Carefully considering each option and its benefits is critical to finding the best fit.
In-house SOCs are the traditional SOC model -- a dedicated group of security professionals are responsible for monitoring, analyzing and protecting against cyber attacks.
A newer option is the virtual SOC, which has two suboptions. An enterprise-run virtual SOC is a SOC that is fully controlled by enterprise employees but hosted in the cloud without the overhead of a physical location. A subscription-based virtual SOC, also known as SOC as a service (SOCaaS), is when enterprises outsource some or all SOC responsibilities to a managed service provider.
The terms can get confusing. Read on to learn more about the two types of virtual SOCs, their benefits and when one might be a better option than the other.
Explaining the virtual SOCs
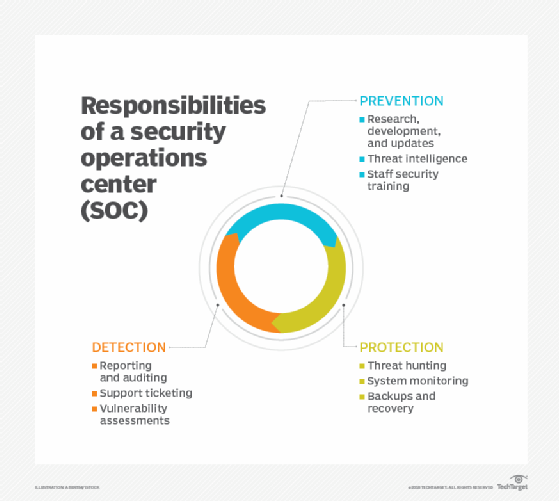
In both iterations, a virtual SOC, also known as SOC 2.0, is an online security command center that is available 24/7, year-round.
Virtual SOCs have all the capabilities and tools that physical SOCs have, including continuous monitoring and implementing tools to improve an organization's security posture through prevention, detection, analysis, response and triage techniques.
Where the two models differ is in the employees. An enterprise-run virtual SOC can be composed of solely company staff or a mix of company staff, on-demand workers and cloud-provided workers. With SOCaaS or an outsourced SOC, either all services can be outsourced to a third party or just some -- for example, some lower-level SOC tasks, such as information gathering, may be outsourced, leaving higher-priority tasks, such as analysis of that information, to the organization's security team.
Virtual SOC benefits
Enterprise-run virtual SOCs are becoming increasingly popular for three main reasons:
- Cost. The costs of building and maintaining a physical SOC is ever increasing. Beyond real estate, the number of employees needed to run the SOC can exhaust budgets. With constantly tightening security resources, CISOs are always on the hook to find ways to reduce Capex and Opex spend. The SOC is always on the CISOs radar to cut expenditures.
- Reliability and availability. Cloud infrastructure has revolutionized modern cybersecurity, especially when it comes to reliability, scalability and availability. In some instances, the expertise and tools needed to maintain uptime and ensure the integrity of a virtual SOC in the cloud far exceed what an enterprise can do in a physical SOC.
- Uniqueness of the environment. The work-from-home era has not only increased BYOD use, but also resulted in these devices being shared at home among family members and housemates. Though enterprise mobile device management software is still prevalent, it becomes nearly impossible to implement under these conditions. The pandemic caused an overnight surge in work-from-home employees, and a large portion of employees' traffic now goes straight to cloud applications versus being routed via the enterprise network first. An in-house SOC team is better able to recalibrate baselines and adjust false positives, which may happen as a result of this shift.
A partly or fully outsourced SOC may be the preferred option for some enterprises for reasons beyond these three benefits. For example, virtual SOCs can help with the following:
- Targets on your back. Attack targets are no longer solely high-net worth organizations, such as banks, or national critical assets, such as power grids. Increasingly, smaller companies and even school districts are being targeted by malicious actors. With neither the budget nor talent to manage or monitor a SOC themselves, many of these businesses and organizations are seeing an outsourced virtual SOC as a viable option.
- Compliance and regulations. In addition, stringent regulations, such as GDPR, CCPA and Privacy Shield, have an element of monitoring, reporting and incident response that must be adhered to and demonstrated to pass security audits. A fully or partially outsourced virtual SOC can be instrumental in helping businesses demonstrate compliance to not only pass audits, but also maintain enduring customer trust.
- The talent gap. A partially or fully outsourced virtual SOC can also help enterprises tackle the current talent shortage. With ransomware becoming more targeted and the number of malicious attacks ever increasing, the need for high-quality security talent who can manage the entire incident lifecycle has never been greater -- nor more difficult. And, with the cybersecurity skills shortage at an all-time high, an outsourced SOC has become the only option for some businesses.
- Aggregate value. Managed virtual SOCs can also provide better security detection and response than SOCs that are in-house or company-run. This can lead to a virtuous cycle: The more data and telemetry a SOC has, the better incident detection, response and remediation the SOC team can provide. Algorithms and human response capabilities will become more accurate. All customers of the managed virtual SOC benefit as a result because the managed SOC provider can gather more data based on the types of attacks it sees across its entire customer base. As a result, the provider can hone its detection and analysis capabilities for all clients.
Bottom line: Today's SOC has various incarnations. Choosing the model that best aligns with your organization's needs and budget requires careful consideration to result in the best outcome for the company and its customers.






