Cybersecurity career path: 5-step guide to success
Taking the lead from ISSA's framework, here's a guide to how you can map out a long and profitable career in cybersecurity.
Cybersecurity career paths have become more formal over the years as security incidents have increased and the skills required to keep companies safe have become more specialized.
Many of the people who entered the field as computer support techs or network administrators with no special training in security have bolstered their skills over time by taking certification courses or going back to college for more education.
The result is that the cybersecurity field now offers distinct career paths with milestones to be met and requirements to fulfill.
One of the best career path diagrams for security professionals has been developed by Information Systems Security Association (ISSA) International. Called the Cyber Security Career Lifecycle (CSCL), the five-step model helps aspiring and professional security experts chart what education, experience and certifications they will need to progress.
The five designations in the ISSA cybersecurity career path model are big buckets with many discrete job titles and skills to learn about. Here's how the career path breaks down, with information on the experience of people at each phase, the time period generally associated with mastering each career phase and the salary ranges for the job titles associated with each level.
Pre-Professional: Getting started in cybersecurity
This category pertains to people with no cybersecurity experience but want to get into the field. While many people in cybersecurity have formal computer science training, there's no reason a person with a music degree or other kind of liberal arts degree couldn't pursue a cybersecurity career.
Simone Petrella, president and co-founder of N2K and CyberVista, now N2K, said former journalists make some of the best threat researchers because they have a background in digging for facts and writing clearly about what they've found after investigating a topic. People looking to switch careers after 20 years in law enforcement or the military are also good candidates for cybersecurity. Many have worked as detectives or investigators at police departments or have gained solid IT and intelligence gathering experience in the military. These are all good backgrounds for success in cybersecurity.
Computer science and business students may want to pursue cybersecurity because they've heard job openings and opportunities for career advancement are abundant. That's true, but career success hinges on having a sincere interest in the topic and a willingness to discover and study the aspect of cybersecurity that most captures your interest.
Entry Level: 1-3 years
Entry-level people often start in computer support or network administration, but people with a business degree or liberal arts degree who are working on security certifications may also find themselves in entry-level jobs.
A common entry point is as an analyst in a security operations center (SOC). The job can be tedious, but after working 12 to 18 months in an SOC and passing some basic certifications, people can start looking to make the next move.
A word of caution at this juncture: Know thyself. Security experts advise beginners to pursue the aspect of security that interests them most. Some people may never make good managers. They are instead hands-on types who work well in task-oriented situations, like penetration testing (pen testing) or threat research and analysis, but aren't interested in managing people.
Job titles: Associate cybersecurity analyst, associate network security analyst, cybersecurity risk analyst, SOC analyst
Education: Bachelor's degree in business or liberal arts; CompTIA Security+
Salary range: $40,000-$80,000
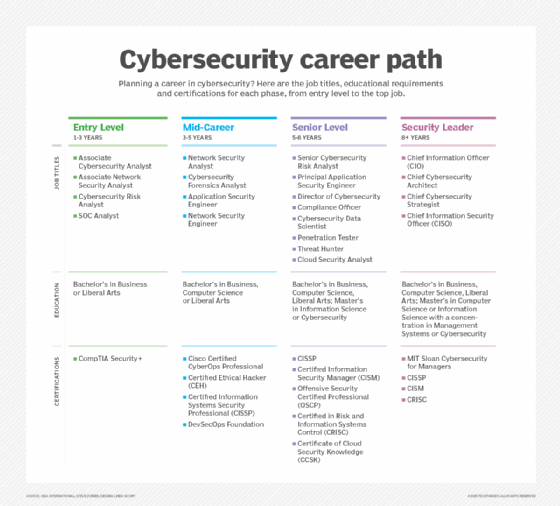
Mid-Career: 3-5 years
At this point in their cybersecurity careers, people have mastered general security principles and have started branching out into the fields that interest them.
Those who started out in networking, for example, may have expanded their knowledge and are now more on the network security or cloud security architect path, while others decided they like being on incident response teams and want to focus more on forensics.
Still others may have programming backgrounds and computer science degrees and have decided that they want to focus on DevSecOps, an area with high demand. This is because developers are typically focused on getting new products out the door quickly, rather than on the security of those products. Programmers who understand how to build security into the entire software lifecycle are coveted by organizations. The DevSecOps Foundation is a good resource.
Job titles: Network security analyst, cybersecurity forensics analyst, application security engineer, network security engineer
Education: Bachelor's degree in business, computer science, liberal arts; Cisco Certified CyberOps Professional, Certified Ethical Hacker, Certified Information Systems Security Professional (CISSP), DevSecOps Foundation
Salary range: $80,000-$105,000
Career guides for cybersecurity
Consult these in-depth guides to cybersecurity certifications, online training and in-demand cybersecurity skills for more ways to advance your cybersecurity career:
Senior Level: 5-8 years
The people at this juncture in the cybersecurity career path are the ones leading threat intelligence teams and heading up pen tests and incident response teams. Many have decided that they are hands-on people who don't aspire to top management and want to focus more on responding to events or working with customers to point out vulnerabilities and develop their security programs.
Others take a risk analysis track and work on explaining business risk to the CISO and top management. Some of these people come from accounting backgrounds and have worked in the accounting departments of banks and top financial firms.
Still others may have technology backgrounds but focus more on compliance and regulatory issues. They may have combined a technical background with some policy courses. For example, someone focused on the EU's GDPR would need a technology background but also some background in international business and policy. And someone who becomes an expert in PCI DSS would have to have solid technology experience and a background in e-commerce security and web development and management. Cyber data scientists at this level are increasingly expected to have knowledge of AI capabilities and applications.
Job titles: Senior cybersecurity risk analyst, principal application security engineer, director of cybersecurity, compliance officer, cybersecurity data scientist, penetration tester, threat hunter, cloud security analyst
Education: Bachelor's degree in business, computer science, liberal arts; master's degree in information science or cybersecurity; CISSP, Certified Information Security Manager (CISM), Offensive Security Certified Professional, Certified in Risk and Information Systems Control (CRISC), Certificate of Cloud Security Knowledge
Salary range: $105,000-$160,000 (top threat hunters can make close to $250,000)
Security Leader: 8+ years
Security leaders -- often called a chief information security officer, or CISO, at large companies with a C-suite -- are seasoned cybersecurity veterans with an ability to manage people and projects. The best CISOs have diverse backgrounds and can come from strong IT training or even the risk departments of banks. While some have worked in risk and compliance, others may have managed a few racks of Windows servers and then worked in network management.
The most traditional path for someone who wants to become CISO would be to earn a computer science degree or a bachelor's degree in business with a concentration in IT management. A master's in computer science with a concentration in cybersecurity also helps but is not required for those with many years in the field.
 Candy Alexander
Candy Alexander
Candy Alexander, CISO and leader of the cybersecurity and risk management practice at consulting firm NeuEon, said the best CISOs also understand business at a deep level. Alexander, a former president of ISSA's international board and chief architect of its CSCL model, said the industry needs people who can talk to senior management in ways they understand instead of talking about network logs and threat pattern. Effective CISOs can explain what the risks are to the business and how security incidents will impact sales, profits, future growth and the company's reputation.
Other security leader jobs that pay top salaries include the following:
- Chief cybersecurity architect. Plans, designs, tests, implements and maintains security systems.
- Chief cybersecurity strategist. Designs cybersecurity programs from the ground up.
Job titles: CIO, chief cybersecurity architect, chief cybersecurity strategist, CISO
Education: Bachelor's degree in business, computer science, liberal arts; master's degree in computer science or information science with a concentration in management systems or cybersecurity; MIT Sloan Cybersecurity for Managers, CISSP, CISM, CRISC
Salary range: $160,000-$265,000 (top people at Fortune 500 companies can make well in excess of $265,000)
Steve Zurier is an independent freelance technology writer covering IT security, networking and cloud computing.







