
Maksim Kabakou - Fotolia
How the BloodHound tool can improve Active Directory security
Auditing Active Directory can be made easier with tools like the open source BloodHound tool. Expert Joe Granneman looks at the different functions of the tool and how it can help.
It may not be commonly known that criminals using ransomware to attack companies are not the elite minds of cybersecurity. They are not performing their own research into zero-day exploits just to encrypt your company's data. That's not to say that these criminals aren't being innovative with their attack techniques; they have just built a business that takes advantage of common security vulnerabilities that exist on many company networks and turns them into profit. The depressing fact is that many of these vulnerabilities are either IT mistakes or completely preventable.
It is not usually the case that the IT admins are lazy or negligent; it usually comes down to priority conflicts due to a lack of human resources, as well as technical tools. They often make choices between keeping the business running and applying security updates. Good commercial security tools can exhaust the IT budget along with management support in a single expensive death blow. It is no wonder that the tasks considered simple IT hygiene, such as patching and secure configuration, are often overlooked and targeted by ransomware.
How attackers threaten Active Directory
One of the most common ransomware attack vectors is caused by using weak authentication. As demonstrated by the recent resurgence in ransomware attacks, from SamSam to LockCrypt, attacks take advantage of internet-exposed services liked Microsoft Remote Desktop with default or easily guessed credentials. They are particularly focused on finding administrative user accounts that enable them to encrypt entire networks at a time. These elevated credentials also help them to destroy volume shadow copies and steal additional passwords from memory. Administrative credentials also enable these attackers to bypass antivirus and upload additional malware to the target network.
IT staff doesn't intend to expose weak administrative accounts to the internet, but if it happens, they were probably under pressure to get a new application running, and exposing the remote desktop protocol to the internet seemed like an acceptable risk. These IT staffers have often lost track of the number of administrative accounts that have been created over the entire life of the network. It is not uncommon to find administrative accounts that have existed for over 10 years with very basic passwords during an assessment.
Red teams have targeted Active Directory for years searching for weaknesses like default credentials that enable them to gain initial access to a network, move laterally, and eventually acquire administrative access. This has led to the development of a number of useful open source offensive tools that map out Active Directory and enable red teams to more quickly identify their targets and chains of attack.
These chains of attack are usually similar to how a ransomware attack will gain an initial foothold and spread throughout a company network. This means that the open source tools that were originally written for offensive operations are also useful for IT administrators looking to defend their networks against ransomware attacks.
The BloodHound tool
One open source tool that is useful for auditing Active Directory is BloodHound. This tool was announced at DefCon 24 as an aid to map out large Active Directory installations with large numbers of trusted domains. The system uses the free version of Neo4j's Graph Platform to store all of the Active Directory data points as relationships between objects instead of a traditional table-based SQL database. The use of the graph platform in the BloodHound tool is well-suited for showing how Active Directory relationships impact users, groups and authenticated sessions. This unique perspective creates visualizations of Active Directory where security risks of weak administrative accounts become instantly obvious.
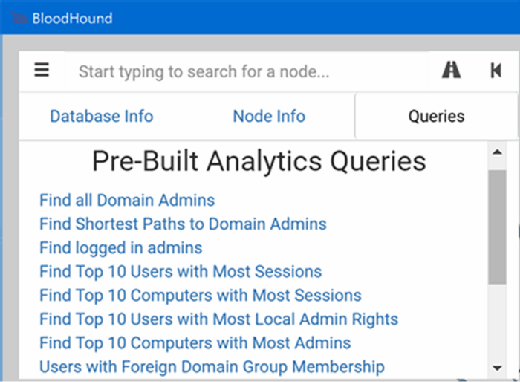
The BloodHound tool uses a PowerShell ingestor script or binary to gather the required information from Active Directory. It can gather more information as an administrator but can also run as a standard user. The BloodHound tool can show how much information is available to the standard user in Active Directory. Once the files created by the ingestor are imported into Neo4j, the relationship data can be quickly analyzed using the built-in queries shown below.
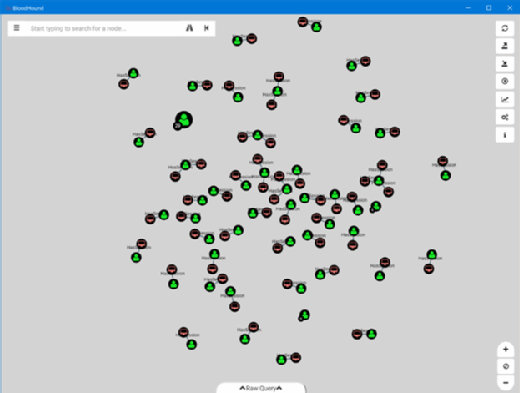
Successful ransomware attacks that affect entire companies must find administrative accounts with weak credentials to launch their attacks as mentioned earlier. The BloodHound tool can visually display all of the currently logged in users who have administrative access. These user accounts all have the potential to be the starting point of a ransomware attack. The screenshot below shows a sample of currently logged in users with administrative access and the computers they are currently using. The users and computers would be identified by BloodHound if this were not sample data.
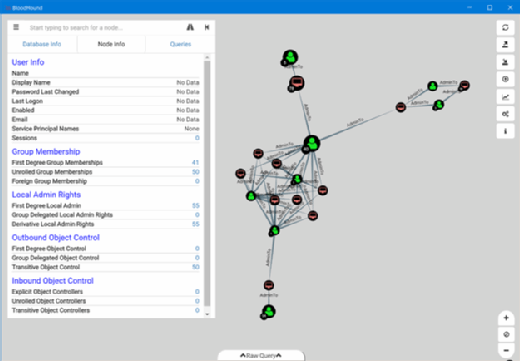
This basic information is useful, but BloodHound takes this concept further by not only identifying the users with administrative permissions, but also the interrelationships formed by these permissions, whether directly applied or a result of group membership. Ransomware often uses a primitive logic to spread throughout the network as well. There can be remnants of text files left behind by ransomware that contain lists of active users pulled from Active Directory during incident response. The ransomware authors use this information to optimize their attacks after compromising administrative credentials from the memory of the first compromised host.
The screenshot below shows how these relationships can be abused to gain further access within the network and simulate a ransomware-style attack. It shows the top 10 users with the most local administrative rights to computers within the domain. If a user has administrative access to a computer where another user account has administrative access to a different set of computers, ransomware will be able to spread across both sets of machines. This can have a multiplicative effect and lead to the compromise of the entire network from an attacker or ransomware. This information can help IT staff identify everywhere that administrative rights have been granted and review the need for that level of access.
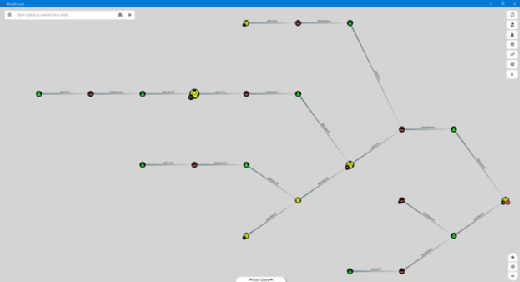
The relationships between different administrative users and groups can be used in an attack chain to eventually acquire Domain Admin credentials. The shorter the attack chain, the more likely the target network is at risk of a successful ransomware attack. Any excessive administrative rights given to users and groups can cascade and create a short attack chain. This visualization allows IT staff to identify and remediate those forgotten groups or misplaced user accounts that had administrative rights for a specific reason at some point in the past. The screenshot below shows the relationships that can be abused to gain administrative access in the example network.
Ransomware is a growing threat to organizational networks that feeds on common vulnerabilities and misconfigurations created by under-resourced or underprioritized IT security initiatives. Weak credentials for long-forgotten administrative user accounts are one of those highly targeted misconfigurations. Organizations must begin to identify and scrutinize the user accounts that have administrative access to limit potential ransomware risks.
Open source tools that were designed for attacking Active Directory can be incredibly useful for defending networks against ransomware by identifying administrative accounts and their interrelationships. Organizations that proactively audit and remediate these administrative account risks using open source tools will keep themselves from being the next ransomware headline.







