10 remote work cybersecurity risks and how to prevent them
Larger attack surfaces, limited oversight of data use and more vulnerable technologies are among the security risks faced in remote work environments.
Despite some mandates for workers to go back to the office in the aftermath of the COVID-19 pandemic, most organizations are sticking with remote work or a hybrid approach. These work-from-anywhere environments might be a boon for employees, but they create headaches for the cybersecurity and IT teams who must contend with the security risks stemming from remote work.
According to a February 2023 survey by Pew Research Center, 35% of workers with jobs that can be done remotely were working from home full time, and 41% had a hybrid schedule combining remote and in-office work. Most CEOs plan to keep such arrangements in place, based on the "C-Suite Outlook 2024: Leading for Tomorrow" report from The Conference Board. Only 4% of the CEOs it surveyed in late 2023, both in the U.S. and worldwide, said they will prioritize a full-time return to the office by workers.
At the same time, the number of cyberattacks against organizations continues to rise. For example, attempted attacks detected by cybersecurity software vendor Armis increased 104% year to year in 2023, it said in a report titled "The Anatomy of Cybersecurity: A Dissection of 2023's Attack Landscape." The combination of cloud, on-premises and remote environments complicates efforts to protect IT systems against attacks, Armis said in the report, which was published in January 2024.
How does remote work affect cybersecurity?
Cybersecurity teams have been beefing up their organization's defenses and adjusting security strategies based on lessons learned after remote work options were widely scaled up during the pandemic's early days, said Colin Troha, cybersecurity managing director at Boston Consulting Group's BCG Platinion unit and the firm's North American leader on cybersecurity.
The new defenses and strategies are designed to counter the security challenges that arose from the expansion of remote work, Troha said. However, many of those challenges remain in play -- and new ones have emerged since then. As a result, many teams "still struggle with getting the right protections and the right security mechanisms in place -- not only for now, but for the future, too," he said.
Armis made a similar point in its report, calling out "the ongoing need to balance the security challenges of hybrid work."
Efforts to do so can be further complicated, though, by cybersecurity staffing issues in organizations. In a 2023 survey conducted by TechTarget's Enterprise Strategy Group and Information Systems Security Association International, a combined 71% of the 301 ISSA members who responded said their organization was being somewhat or significantly affected by the ongoing shortage of skilled cybersecurity professionals.
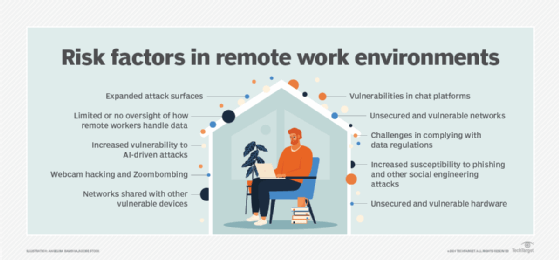
Common remote working cybersecurity risks
Working remotely, or mixing that and in-office work, can raise the risk of data breaches and different types of cyberattacks for various reasons, according to Troha and other security experts. Here are 10 of the most prominent cybersecurity risks associated with remote work and the work-from-anywhere movement.
1. Expanded attack surfaces
With more employees working remotely, the attack surface in organizations has become larger. They have more endpoint devices, networking connections and software to secure, all of which greatly increase the workload for security staffs that are often stretched thin, said Kumar Avijit, cloud and infrastructure practice director in the IT services team at research firm Everest Group. "That also adds to the complexity of what [teams] must secure," he added.
2. Limited or no oversight of how remote workers handle data
In recent years, many security teams have implemented tools that prevent workers from downloading sensitive information to their local devices, yet data loss due to remote work is still a real problem, Troha said. In fact, he and other consultants said work-from-anywhere environments increase the risk of data breaches and leaks even in organizations with strong data protection policies and procedures. With security teams having less direct oversight of employees outside the office, remote work heightens the chances of both unintentional and malicious exposure or loss of corporate data. For example, workers might have sensitive data on their screens that could be seen by other people -- whether family members and visitors at home or strangers passing by at a public location. Also, disgruntled employees leaving for another job can easily snap photos of proprietary data on their screens when working remotely -- something they likely wouldn't do in an office where they might be noticed.
3. Challenges in complying with data regulations
Organizations might find that regulatory compliance is more challenging in work-from-anywhere environments. Remote workers can access and transport data in ways that violate the growing list of data privacy and protection laws, as well as contractual obligations with other organizations, said Scott Reynolds, senior director for enterprise cybersecurity at professional association ISACA. "You may have contracts that say this data may only be processed in the EU or the U.K.," he said. "But, if you have workers coming to the U.S. or working remotely elsewhere and they start working on that data, that introduces a compliance risk."
4. Increased susceptibility to phishing and other social engineering attacks
Phishing and other types of social engineering attacks are a threat whether workers are in the office or remote. However, such attacks tend to be more successful when aimed at remote workers, said Sushila Nair, vice president of security services at NTT Data Services and a member of ISACA's Emerging Trends Working Group. "Research has found that people working from home can be more distracted and they're more likely to click on suspicious links," she said. Moreover, remote workers can't verify that email messages purportedly sent by colleagues are legitimate as easily as they could if working in the same office with others. That increases the chance they fall victim to phishing emails disguised as requests for passwords or data from co-workers and executives, as well as customers, business partners and other reputable organizations.
5. Increased vulnerability to AI-driven attacks
Attackers now are also using AI -- in particular, generative AI tools -- to automate social engineering attacks, said Ed Skoudis, president of the SANS Technology Institute, a college that's part of cybersecurity training, education and certification firm SANS Institute. Remote workers, especially ones who don't regularly meet in person with others, might have an even harder time distinguishing such attacks from legitimate communications. Without strong working relationships between them and co-workers, for example, they might not detect the increasingly subtle differences in language used by attackers impersonating colleagues with the help of AI tools. In addition, generative AI enables attackers to create and carry out phishing campaigns much faster than they could on their own, increasing the number of attacks that both remote and in-office workers can face.
6. Unsecured and vulnerable hardware
The combination of increased remote work and longstanding BYOD policies means many people use personal devices to do their jobs, regardless of whether they have the skills to adequately secure and protect their laptops and smartphones, said Jim Wilhelm, principal in the cybersecurity services practice at KPMG. Organizations can require employees to take certain steps, such as changing default passwords, but security leaders don't always have visibility into whether workers fully comply with such mandates. "CISOs have to hope their workers are following their security policies," said Steven McKinnon, associate director for financial fraud and investigation on the cyber solutions team at consulting firm Guidehouse.

7. Unsecured and vulnerable networks
Remote work also increases the chance that employees use unsecured networks, such as public Wi-Fi. Even home networks are often vulnerable to attacks. "Corporations can secure their own networks, but they can't know how any network that's not corporately managed -- whether it's a network in a worker's house or at their local cafe -- is configured," Reynolds said. "They're essentially relying on a third party to implement the needed network security."
8. Networks shared with other vulnerable devices
The fact that other users tend to be on public Wi-Fi and home networks further expands cybersecurity risks, Troha said. If someone else's device is poorly secured, an attacker could use it as a conduit into the network and then ultimately into a remote worker's device, too.
9. Webcam hacking and Zoombombing
Early in the pandemic, attackers exploited the increased use of video conferencing and online collaboration platforms without strong security controls. Cybercriminals sabotaged remote meetings and online conferences and prowled around undetected on Zoom and other platforms to obtain information to use to their advantage. Skoudis said the risk of such incidents still exists, although it has been mitigated by the defensive measures that security teams rushed into place in response to those incidents.
10. Vulnerabilities in chat platforms
More commonly now than trying to infiltrate meetings, attackers are targeting chat platforms used by employees. "They're getting into an organization's chat, where they'll watch and monitor for months to see how people are interacting," Skoudis said. "Then, they'll build relationships, build trust and gather information." Remote workers who only or mostly engage with colleagues through the chat function tend to be less likely to detect an attacker's subterfuge, he added.
Cybersecurity best practices in remote work environments
The following security management best practices can drastically reduce an organization's chances of suffering a costly -- and sometimes devastating -- cyberattack that takes advantage of weaknesses and vulnerabilities in remote work environments:
- Implement basic security controls. "Make sure you have your security fundamentals nailed down," McKinnon said. "For example, have an inventory of assets. Communicate your policies to your employees, and make sure they understand those policies because the security risks [related to remote work] are even more prevalent now." Other expert-recommended basic steps include using VPNs to access enterprise systems; ensuring devices that access the enterprise network have antivirus software; following a strong password policy that requires unique passwords for different sites; and using encryption to protect sensitive data and cloud-based file sharing to keep data off worker devices.
- Strengthen the corporate data security and protection program. "Know where your digital information is, what information you're collecting, where your crown jewels are stored and what you're doing to protect the data," Reynolds said. He and others said security leaders also must develop comprehensive data security awareness training for employees so they are better equipped to safeguard data wherever they're working. That's a key part of building a broader cybersecurity culture in an organization.
- Establish a strong vulnerability management program. Effective vulnerability management also bolsters remote working cybersecurity processes. Use a risk-based approach to quickly address vulnerabilities that present the highest risks and reduce the overall number of unpatched vulnerabilities that attackers could exploit. Doing so can also aid in attack surface management initiatives aimed at better protecting IT assets that attackers are likely to target.
- Implement a zero-trust framework. All remote users and devices should be required to verify that they're authorized to access the enterprise network and then individual systems, applications and data sets. A zero-trust security approach denies access to IT systems by default and gives authenticated users access to only the ones they need to do their jobs.
- Deploy user behavior analytics (UBA) tools. UBA -- or user and entity behavior analytics (UEBA) as it's increasingly known -- is a key component of the zero-trust framework. The technology uses machine learning and data science to identify and understand a user's typical pattern of accessing enterprise systems, and it flags suspicious activities that could indicate user credentials have been compromised.
- Ensure proper cloud configurations and access. Misconfigurations are a leading cause of security incidents in public cloud infrastructure. Security teams should work with the IT operations staff to take measures to eliminate glitches, gaps or errors that could expose a remote work environment to risks during cloud migration and operation. They should also institute sensible user access controls in cloud-based systems.
- Update policies and procedures to address the heightened security risks associated with remote work. CISOs and their teams, along with IT and data privacy professionals, must ensure they're updating their organization's security policies, procedures and protections to address the new and evolving threats that affect remote and hybrid workplaces. For example, Skoudis said IT administrators need to be more diligent about managing access to corporate chat functions by taking steps such as disabling worker access when employees leave the company, implementing MFA for chat and giving workers a mechanism to report suspicious chat activity. Those tasks often weren't a high priority before remote work became a standard option, he added.
- Enable relationships and in-person connections. Skoudis said organizations should create opportunities for remote and hybrid workers to build relationships with their bosses and teammates, as well as meet in person -- especially when onboarding new employees. Such connections might enable remote users to better recognize social engineering attacks and bolster their overall attentiveness to help keep the organization secure.
Mary K. Pratt is an award-winning freelance journalist with a focus on covering enterprise IT and cybersecurity management.






