
stock.adobe.com
Mitigate threats with a remote workforce risk assessment
Risk assessments are more necessary than ever as organizations face the challenge of protecting remote and hybrid workers alongside in-office employees.
The importance of a risk assessment cannot be denied. Identifying and mitigating the risks, threats and vulnerabilities that exist within IT infrastructures in a timely manner is crucial to lessen the impact of these hazards and prevent them from seriously disrupting business operations.
Risk assessments have long been essential elements in good IT planning and management. Now, in the wake of the global COVID-19 pandemic, many organizations must perform a new type of risk assessment to keep operations secure: a remote workforce risk assessment.
Let's examine the different types of risks, threats and vulnerabilities IT management must address to minimize disruptions and maintain employee productivity, and explore how a remote workforce risk assessment fits into the process.
Internal vs. external risks
From an IT perspective, risks, threats and vulnerabilities are initially defined as internal or external. For example, an internal risk may be the inability to provide IT services to maintain existing systems and services, while external risks include disruptions to utilities, critical infrastructure damage and destruction, and acts of God.
Internal threats, on the other hand, include loss of power, equipment failure, theft of equipment and vandalism. External threats include loss of commercial power, loss of network services and unauthorized access to data centers.
Internal vulnerabilities include systems that are not properly patched, backup plans that are not tested and inoperative security access controls. External vulnerabilities include not using external security cameras or lighting, lightning arresters and emergency backup power.
The importance of risk assessments for remote workers
Regular risk assessments identify issues that must be addressed, identify opportunities to minimize the likelihood of risks occurring and define strategies to mitigate the severity of potential risks if one should occur.
These same assessments must be considered when it comes to remote and hybrid workers. The issue is compounded because employees today work in many different locations, as opposed to a single office. As a result, risk assessments for remote and hybrid employees must be performed as individual activities and must follow a consistent process.
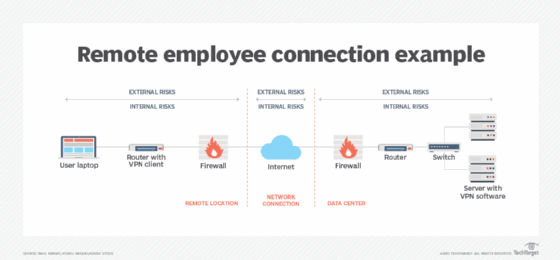
The 3 risk assessments in a remote employee risk assessment
When adapting or creating a risk assessment for remote workers, internal and external risks must be identified and addressed in three areas:
- data center;
- network resources connecting remote employees; and
- remote worker's location.
Data center assessments examine internal and external risks, threats and vulnerabilities in the data center and infrastructure of a company. Assessing risks, threats and vulnerabilities at data centers should be performed regularly based on the size and complexity of the company. Larger and more densely populated data centers should be assessed more frequently, perhaps quarterly or even monthly. These assessments may be affected by the number of remote workers and their demand for IT resources, such as applications, data files and databases.
Results of these assessments can be used to fine-tune system administration, incident response, backup and recovery, data protection and management, disaster recovery, physical and local access security, and environmental management activities.
Network risk assessments can also be affected by the number of remote workers. The demand for greater bandwidth means more frequent reviews of bandwidth usage, response times and overall network throughput.
The internet is the network service used most frequently by workers to gain access to services and applications, but managing internet risks is generally outside an organization's control. The same holds true for managing risks associated with workers accessing the internet through local telecom operators. Yet, users can proactively monitor network performance using a variety of specialized tools. They can also contact network providers -- both ISPs and local telecom operators -- in the event performance anomalies are detected.
Remote worker assessments are the final leg of the process. The risk factors an enterprise assesses can be tweaked to more accurately reflect a remote workforce risk assessment strategy. Employees working at home or at an alternate office location must be diligent in managing and maintaining their systems and remote access resources. This can be done in partnership with IT staff and help desk teams assigned to manage remote communications activities. Employees working remotely can face external risks that go beyond technology issues -- among them, dealing with young children and other family members, as well as tending to health issues and mental wellness. Many of these issues have emerged from the pandemic and challenge employees and organizations alike.
How to conduct a simple risk analysis
Several metrics are examined when assessing risk, including the likelihood of an event occurring, the impact on the organization and its employees, the severity of the impact and the resources -- for example, funding, equipment and people -- needed to mitigate the risk.
Using a consistent scale for quantification can help evaluate and assess a risk, threat or vulnerability. The table below presents a simple risk analysis metric in which a specific risk, threat or vulnerability is evaluated by rating factors on a scale of 0.0 to 1.0:
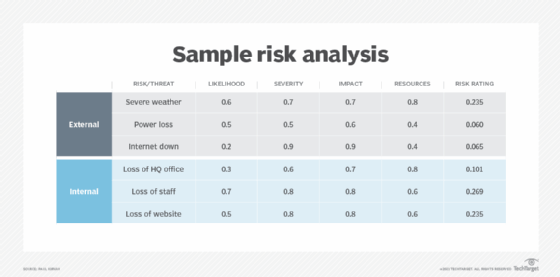
This sample's risk rating metrics are the following:
- Likelihood: 0.0 (unlikely) to 1.0 (absolutely will occur)
- Severity: 0.0 (no damage) to 1.0 (total destruction)
- Impact: 0.0 (no impact) to 1.0 (total loss)
- Resources: 0.0 (none needed) to 1.0 (extremely costly and resource-intensive)
Values for these metrics can be obtained from a variety of sources, such as risk tables, insurance companies and actuarial tables. They can also be estimated based on experimental data.
The last column of the sample table includes risk ratings, which can be used to identify the risks, threats and vulnerabilities that need the most urgent attention. The risk ratings based on calculated score are the following:
- 0.000 to 0.150 = low to minimal business risk indicated
- 0.160 to 0.200 = moderate to high business risk indicated
- 0.210 to 0.250 = serious business risk indicated
- 0.260 to 0.300 = catastrophic business risk indicated
Final considerations
Performing risk assessments that involve remote and hybrid employees is essential in today's dispersed workplace. While the process is largely the same as for other risk assessments, modifying processes to accommodate the unique risks, threats and vulnerabilities associated with remote working can help prevent businesses from experiencing downtime, lost revenue and productivity, and more.





