
stock.adobe.com
Threat intelligence frameworks to bolster security
Organizations have many threat intelligence frameworks to work with, each with its own advantages. From for-profit to nonprofit, here's help to figure out which ones you need.
Threat intelligence frameworks are everywhere. From government, R&D and industry organizations like Mitre, NIST, CISA, SANS and ISACA to pretty much every vendor from Accenture to Zscaler, organizations take slightly different approaches to threat intelligence.
The only thing they all agree on is that cybersecurity organizations need threat intelligence. And they're right. Nemertes' 2019-20 "Cloud and Cybersecurity Research Study" revealed cybersecurity organizations that subscribe to threat intelligence feeds are 58% more likely to have security metrics that place them in the success group, as measured by median total time to contain (MTTC) a security incident. (Nemertes defines the success group as those companies with an MTTC of under 20 minutes, placing them in the 80th percentile of all organizations we studied.)
Here are some questions every organization should consider. What are some of the primary cyber threat intelligence frameworks to consider? How have they evolved over the past few years? And, most importantly, how should cybersecurity professionals engage with these frameworks?
Threat intelligence frameworks to evaluate
A good place to start assessing cyber threat intelligence frameworks is with industry organizations and consortia, including for-profit, not-for-profit, private sector and governmental. These organizations tend to have the best strategic vision of threat intelligence and can help provide the foundation for a solid threat intelligence operation.
Mitre ATT&CK
It's important to note that the Mitre ATT&CK framework isn't specifically a threat intelligence framework. It's a model for describing the actions an adversary may take to compromise and operate within an enterprise network.
One of the benefits of aligning with Mitre ATT&CK, however, is that it is a nonprofit federally funded R&D center that serves as a constantly expanding consolidation point for known tactics, techniques and procedures used by attackers. According to Mitre, the organization incorporates information on cyber adversaries gathered through Mitre ATT&CK research, as well as from other disciplines, such as penetration testing and red teaming, to establish a collection of knowledge characterizing the activities adversaries use against enterprise networks. The organization aligns the attacks to points on the seven-stage Cyber Kill Chain, which it credits to Lockheed Martin.
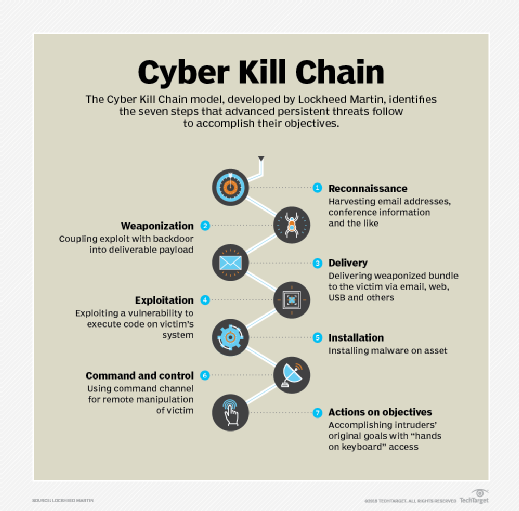
Although Mitre ATT&CK explicitly disavows claims to comprehensiveness, it is one of the most comprehensive attack databases in existence, since organizations are constantly updating it with new information. As a result, cybersecurity professionals should rely on Mitre ATT&CK data as part of their overarching threat intelligence efforts.
CISA (formerly CERT)
The Cybersecurity and Infrastructure Security Agency (CISA) is the U.S. Department of Homeland Security organization that, in 2018, absorbed the Industrial Control Systems Cyber Emergency Response Team and U.S. Computer Emergency Readiness Team. CISA alerts (formerly CERT alerts) provide nonreal-time but authoritative insight on known attacks, along with guidance on remediation.
Cybersecurity professionals should be sure to subscribe to CISA alerts. Weekly alert bulletins are also available.
The SANS Institute
The SANS Institute is a for-profit training organization that codifies best practices from Mitre ATT&CK and others. SANS holds annual summits on threat intelligence. The most recent took place in January. Some key takeaways from the 2021 SANS Institute summit included a discussion of upcoming threats, data structures for capturing threat intelligence, how to convert threat intelligence data into actionable next steps and how to incorporate risk into threat intelligence.
Cybsersecurity professionals should review course offerings from SANS and consider signing up for courses and events of interest, including the annual threat intelligence summit.
ISACA chapters
ISACA is a 54-year-old global industry consortium that focuses on information governance and security. The organization has more than 200 chapters in more than 80 countries that provide members with education, resource sharing, advocacy and professional networking. Like SANS, ISACA offers events, training and professional certification.
ISACA provides guidance around threat hunting, including webinars, white papers and coursework. Cybersecurity professionals should consider signing up for courses and events of interest, including its annual threat intelligence summit.
Industry-specific threat intelligence organizations
Each vertical industry may or may not have organized its own security organization, with a greater or lesser focus on threat intelligence. The financial services industry, for example, has the Financial Services Information Sharing and Analysis Center (FS-ISAC), which is a global cyber intelligence sharing community solely focused on financial services. FS-ISAC has its own intelligence platform, resiliency resources and peer-to-peer network of experts to anticipate, mitigate and respond to cyber threats.
Cybersecurity professionals should research industry-specific threat intelligence organizations and incorporate these into their day-to-day operations.
Vendor threat intelligence frameworks and services
Above and beyond the industry organizations, virtually every cybersecurity vendor provides its own threat intelligence framework or feed. For instance, Microsoft has the Microsoft Threat Intelligence Center that collects threat intelligence and aggregates data from sources such as first-party threat intelligence feeds (honeypots, botnets, etc.); third-party sources, such as other vendors' threat intelligence feeds; and human analysts.
Palo Alto Networks offers MineMeld, an open source threat intelligence processing framework that can be used to collect, aggregate and filter indicators from a variety of sources and make them available for consumption to a range of platforms and to Palo Alto Networks' security platforms.
The CrowdStrike Falcon X cyber threat intelligence platform provides a broad range of technical intelligence data – particularly, but by no means exclusively, around nation-state attacks -- as well as tactical and operational remediation recommendations, augmented by dedicated intelligence analysts.
FireEye's Mandiant incident response consultancy provides threat intelligence based on the company's work with clients as part of its remediation work.
Kaspersky Lab has a portfolio of threat intelligence services it is planning to integrate into a single platform that also includes third-party integrations.
Fortinet's FortiGuard Labs is the company's threat intelligence and research organization. It provides proven threat intelligence based on its millions of global network sensors that monitor the worldwide attack surface and employs AI to mine that data for new threats.
These are just a few examples of the many vendor-provided threat intelligence services. Cybersecurity professionals should plan to select one or more such services and integrate that service into their operational cybersecurity.
Taking the right 5 steps
In summary, when it comes to threat intelligence services and frameworks, cybersecurity practitioners should take the following five steps:
- If you haven't already, familiarize yourself with the Mitre ATT&CK framework and how to use it.
- Register for and participate in the SANS Institute Threat Intelligence Summit.
- Subscribe to CISA advisories.
- Investigate ISACA chapters and industry-specific cybersecurity organizations.
- Assess a portfolio of threat intelligence frameworks, platforms and services from vendors, and select from among them.







