
gosphotodesign - Fotolia
What to do when IPv4 and IPv6 policies disagree
Unfortunately for enterprises, IPv4 and IPv6 policies don't always agree. Fernando Gont examines the differences between these two security policies, as well as some filtering rules.
The most common IPv6 deployment strategy for network servers is the so-called dual stack, in which IPv6 is deployed along with IPv4 and servers become available over both IPv4 and IPv6.
Operating a network that employs two internet protocols -- IPv4 and IPv6 -- generally implies that network configuration needs to be replicated for the newly-deployed IPv6 -- that is, the network must be configured so that IPv6 can operate like IPv4. This network configuration not only includes aspects such as enabling IPv6 routing and incorporating IPv6 information in the domain name system, but also the enforcement of network security policies via packet filtering.
In most common scenarios, IPv6 security policies mirror their IPv4 counterparts. After all, both IPv4 and IPv6 are just internet protocols.
Therefore, they include some specific protocol-dependent issues and security policies, such as those specifying which network services are exposed on the public network, and tend to be agnostic to the underlying network-layer protocol. There is generally no reason for a network server to offer a service over one internet protocol and not the other.
Configuration of security policies
One might expect that security policies enforced via packet filtering rules based on transport layer information -- such as allow incoming packets destined to port 80 -- would be specified in a network layer-agnostic manner. However, many network devices, including security devices, typically require that a filtering rule not only specify the relevant transport-layer information -- such as transport protocol port numbers -- but also the specific network layer protocol for which the rule should be applied, such as IPv4 or IPv6.
This means that in most common dual-stack scenarios, every filtering policy for a specific port number will result in two separate filtering rules: one for the IPv4 case and another for the IPv6 case. As a result, it wouldn't be hard to expect that, on occasion, administrators may simply fail to duplicate such rules; hence, mismatches in the packet filtering policies for IPv4 and IPv6 can occur.
One may expect security policies to be more thoroughly applied in the IPv4 world as a result of sites failing to duplicate/mirror packet filtering rules for IPv6 when the protocol is deployed. However, I presented research at the Hack In Paris 2018 security conference that indicates that the aforementioned guesswork and logic does not apply in the real world.
IPv4 and IPv6 security policies
The study essentially evaluated the IPv4 and IPv6 security policies of a large number of web servers with the goal of identifying possible mismatches between the two. Each of the web servers was port scanned on each of their IPv4 and IPv6 addresses and the results of the port scans were compared.
The following figure illustrates the percentage of sites that exhibited different security policies over IPv4 and IPv6 considering the number of ports that were found in different states over the two internet protocols.
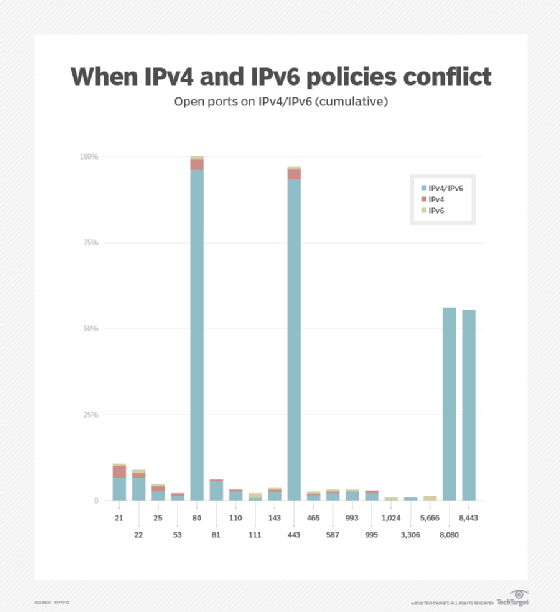
The figure shows that roughly 85% of the websites exhibited the same security policies over both IPv4 and IPv6. On the other hand, 15% of the websites exhibited different security policies over the two network protocols, with most of them exhibiting a mismatch for up to five different port numbers -- that is, for that 15% of web servers, between one and five ports were found in different states depending on the underlying internet protocol.
The figure also illustrates the frequency with which different port numbers were found to be open on the port scanned websites.
The results of the port scan are illustrated in the bar chart above and indicate, for each open port, whether the port number was open only over IPv4, only over IPv6, or over both IPv4 and IPv6.
To make the differences in filtering policies more evident, the following figure illustrates the frequency of policy mismatches for each port number; that is, the percentage of port scanned sites that exhibited a port open only over IPv4 or IPv6, but not over both internet protocols.
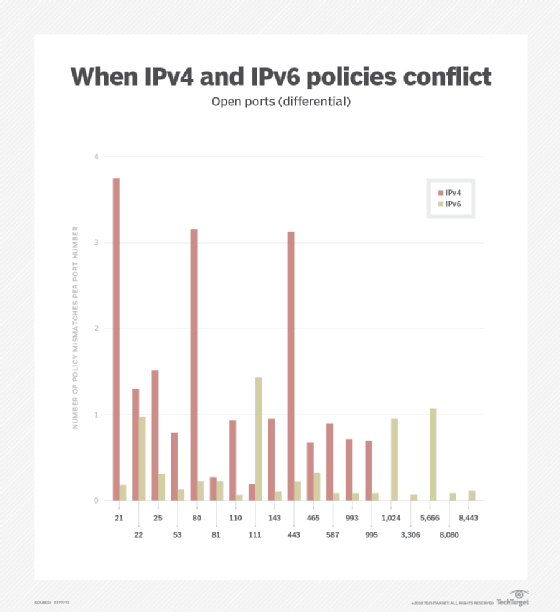
What is interesting from the port scanning results is that, while there are evident mismatches in the security policies applied for IPv4 versus the policies applied for IPv6, you cannot really argue that the policies for one of the internet protocols are more permissive than the those applied to the other. In fact, the study shows that the policies seem to be dependent on the port numbers in question, with some ports being more open over IPv4, while others are more open over IPv6.
Finally, for servers that were available over multiple IPv4 addresses and multiple IPv6 addresses, the study also found that while there were virtually no policy mismatches for different IPv4 addresses on the same server, there was a small percentage of mismatches among the different IPv6 addresses of the same website.
Implications for pen testers
When assessing which services are being offered by a given server, it is not unusual for pen testers to port scan a server over any one of the addresses, but not over all of them.
Based on the policy mismatches found for IPv4 and IPv6, and for different IPv6 addresses on the same servers, it is clear that when assessing which services are being offered by a server, the server in question should be port scanned over all of the IPv4 and IPv6 addresses available.
More homogeneous security policies
An obvious takeaway for network and security administrators is that security policies should be more homogeneously applied to both IPv4 and IPv6, and that the enforcement of security policies on both internet protocols should become part of normal operation and management procedures.
It is also advisable for sites that don't currently support IPv6 to apply IPv6 packet filtering policies that are similar to those applied to the IPv4 counterparts. This way, when IPv6 is finally deployed on those sites, the servers and other network elements will not be caught off guard.
Conclusion
Recent studies have indicated that mismatches between IPv4 and IPv6 security policies are rather common. Network and security administrators must take action to ensure that the policies applied to both protocols are homogeneous. These common mismatches warrant that, when port scanning a site as part of a penetration test, for example, all of the available addresses must be subject to port scans, as the results for different addresses and different internet protocols may differ.






