remote access
What is remote access?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection.
Remote access enables users to connect to the systems they need when they are physically far away. This is especially important for employees who work at branch offices, are traveling or telecommute.
Remote access enables remote users to access files and other system resources on any devices or servers that are connected to the network at any time. This increases employee productivity and enables employees to better collaborate with colleagues around the world.
A remote access strategy gives organizations the flexibility to hire the best talent regardless of location, remove silos and promote collaboration between teams, offices and locations.
Technical support professionals can use remote access to connect to users' computers from remote locations to help them resolve issues with their systems or software.
One common method of providing remote access is via a remote access virtual private network (VPN) connection. A VPN creates a safe and encrypted connection over a less secure network, such as the internet. VPN technology was developed to enable remote users and branch offices to securely log into corporate applications and other resources.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
For example, traditional remote access before the wide availability of internet connectivity was accomplished using terminal emulation software that controlled access over a hardware modem connected to a telephone network.
Today, remote access is more commonly accomplished using:
- Software: Using a secure software solution like a VPN.
- Hardware: By connecting hosts through a hard-wired network interface or Wi-Fi network interface.
- Network: By connecting via the internet.
Remote access VPNs connect individual users to private networks. With a remote access VPN, each user needs a VPN client capable of connecting to the private network's VPN server.
When a user is connected to the network via a VPN client, the software encrypts the traffic before it delivers it over the internet. The VPN server, or gateway, is located at the edge of the targeted network and decrypts the data and sends it to the appropriate host inside the private network.
A computer must have software that enables it to connect and communicate with a system or resource hosted by the organization's remote access service. Once a user's computer is connected to the remote host, it can display a window with the target computer's desktop.
Enterprises can use remote desktops to enable users to connect to their applications and networks remotely. Remote desktops use application software -- sometimes incorporated into the remote host's operating system (OS) -- that enables apps to run remotely on a network server and be displayed locally at the same time.
Users can securely access on-premises and cloud applications and servers from anywhere, on any device with a variety of authentication methods, including remote single sign-on, which gives users easy and secure access to the apps they need without configuring VPNs or modifying firewall policies.
In addition, organizations can use multifactor authentication to verify a user's identity by combining multiple credentials unique to one person.
What are the types of remote access?
Traditionally, enterprises used Modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
Broadband provides remote users with high-speed connection options to business networks and to the internet. There are several types of broadband, including the following:
- Cable broadband shares bandwidth across many users and, as a result, upstream data rates can be slow during high-usage hours in areas with many subscribers.
- DSL (Digital Subscriber Line) broadband provides high-speed networking over a telephone network using broadband modem tech. However, DSL only works over a limited physical distance and may not be available in some areas if the local telephone infrastructure doesn't support DSL technology.
- Cellular internet services can be accessed by mobile devices via a wireless connection from any location where a cellular network is available.
- Satellite internet services use telecommunications satellites to provide users internet access in areas where land-based internet access isn't available, as well as for temporary mobile installations.
- Fiber optics broadband technology enables users to transfer large amounts of data quickly and seamlessly.
What are remote access protocols?
Common remote access and VPN protocols include the following:
- Point-to-Point Protocol (PPP) enables hosts to set up a direct connection between two endpoints.
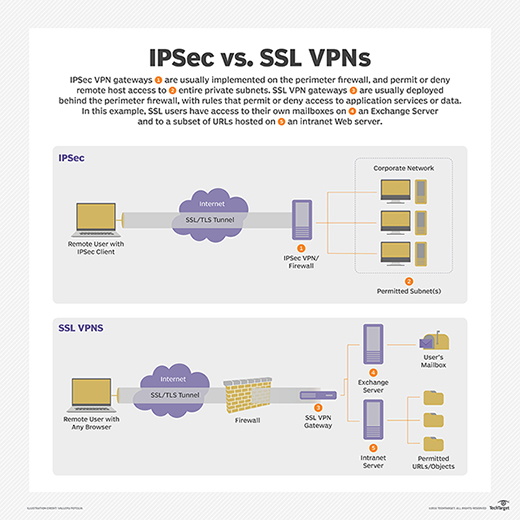
- IPsec -- Internet Protocol Security -- is a set of security protocols used to enable authentication and encryption services to secure the transfer of IP packets over the internet.
- Point-to-Point Tunneling (PPTP) is one of the oldest protocols for implementing VPNs. However, over the years, it has proven to be vulnerable to many types of attack. Although PPTP is not secure, it persists in some cases.
- Layer Two Tunneling Protocol (L2TP) is a VPN protocol that does not offer encryption or cryptographic authentication for the traffic that passes through the connection. As a result, it is usually paired with IPsec, which provides those services.
- Remote Authentication Dial-In User Service (RADIUS) is a protocol developed in 1991 and published as an Internet Standard track specification in 2000 to enable remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service.
- Terminal Access Controller Access Control System (TACACS) is a remote authentication protocol that was originally common to Unix networks that enables a remote access server to forward a user's password to an authentication server to determine whether access to a given system should be allowed. TACACS+ is a separate protocol designed to handle authentication and authorization, and to account for administrator access to network devices, such as routers and switches.







