adware
What is adware?
Adware is any software application in which an advertising banner or other advertising material displays or downloads while a program is running. The ads are delivered through pop-up windows or bars that appear on the program's user interface. Adware is commonly created for PCs, but mobile devices may also be targeted for adware exploits.
Legitimate adware is deployed to help software developers recover development costs. It can also be used to reduce or eliminate the cost of software for users. But, in some cases, the ads contain cybersecurity threats or lead users to a malicious webpage.
How does adware work?
Adware is placed in an existing application on a user's device via a security vulnerability. Users can also download it -- usually unknowingly. This can happen when users do one of the following:
- download an application with adware in it; or
- use software with vulnerabilities that adware authors can exploit.
The goal of adware is to get users to click on or otherwise engage with advertisements. Adware developers and distributors make money when users click on the online advertising that their adware serves. There is legitimate adware that users consent to, but in many cases, it is unwanted. Adware is often just a nuisance, but it can contain malicious threats.
Types of adware
The two main types of adware are legitimate and malicious. There is a gray area in between the two when legitimate adware unintentionally creates vulnerabilities.
Legitimate adware
Legitimate adware is downloaded with the user's express consent. Users download this form of adware knowingly and will usually get something in return. They may get a discount or free software in exchange for receiving the adware. The ads help cover the cost of developing the software or let the developer provide the product free.
For example, some software is offered either free, as an advertising-supported version, or as a paid version without advertisements. Users wanting an ad-free experience can buy the paid version.
Malicious adware
Deceptive or abusive adware makes it difficult for the user to refuse consent or uses deceptive means to gain the user's consent. For example, it may bombard the user with unwanted advertisements or make it difficult to opt out of unwanted third-party software.
Adware is considered malicious only if it is designed with the intent of delivering malicious software to the user. However, some legal adware may unintentionally create vulnerabilities that malware can take advantage of.
Some types of malicious adware include the following:
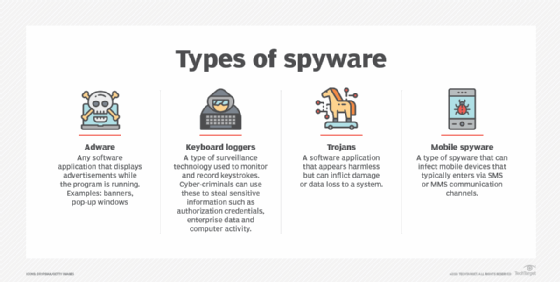
- Spyware. Adware often includes code that tracks and records users' personal information and internet browsing habits. This data may be used with the user's consent to display ads that are tailored to their interests. But the software is classified as spyware if it is done without the user's knowledge and authorization. User data collected in this manner is often sold to third parties. These intrusive practices have prompted an outcry from computer security and privacy advocates, including the Electronic Privacy Information Center.
- Potentially unwanted programs (PUPs). Malicious adware or spyware may be bundled in with free software or Shareware programs and utilities downloaded from the internet. Users visiting an infected website can end up with malicious adware surreptitiously installed on their device. Adware is often flagged by antimalware programs as a PUP whether the adware program in question is malicious or not.
- Man-in-the-middle (MitM) attacks. Adware can also be used to execute MitM attacks. These attacks redirect user traffic through the adware vendor's system, even over secure or encrypted connections. The communicating parties believe they are exchanging information over a secure connection, while the attacker is able to collect and manipulate sensitive information as the conversation takes place.
What is mobile adware?
Mobile adware infects a mobile device. Like other adware, it finds its way onto the device in one of two ways:
- A downloaded application. This happens through a third-party app store, which may have fewer protections than bigger-name ones, like the Apple Store. The adware comes embedded in the application and displays persistent ads when the software is in use.
- A browser. Just as on a computer, adware takes advantage of a JavaScript exploit that enables pop-ups in a web browser.
Some mobile adware types are more harmful than others. Adware that inundates the user with spam and pop-ups is a nuisance but is relatively harmless. Ad fraud, click fraud and ad clicker software are harmful types. They click on ads without users knowing and cause them to subscribe to premium paid services without the user's knowledge.
How do you detect adware?
Some indications that a mobile or desktop device is infected with malicious adware include the following:
- advertisements appear in unusual places;
- new toolbars, plugins or extensions appear in a user's web browser;
- new, unwanted applications appear on a user's home screen;
- web searches redirect to advertising websites or sites other than expected in what is known as browser hijacking;
- ads inside of pop-up windows appear and cannot be easily closed -- they may pop up continuously and overwhelm users;
- the device runs slowly; and
- the browser application runs slowly or crashes.
Mobile-device specific signs of adware include the following:
- a spike in data usage;
- the battery drains faster than expected; and
- higher-than-expected data usage bills.
How do you remove adware?
Users can manually remove adware from a device by identifying the name of the adware program and using the device's application maintenance utility to remove the program. This requires that the user know the name of the adware, which can be difficult to identify. Also, if the adware has a resuscitator, it can reinstall itself automatically even after it has been uninstalled.
Cybersecurity tools can also be used to remove adware. Most endpoint security suites have the ability to scan for and remove adware, spyware and other malware programs. A number of free software applications, such as Adaware's Ad Block, are available to help computer users identify and remove malicious programs. Pay-per-use services are also available, such as Bitdefender's Adware Removal Tool.
How do you prevent adware?
Prevention is the best defense against adware. To avoid infections, users should follow these guidelines:
- Be discerning about any software downloaded; read reviews of applications to help decide if they are legitimate.
- Be wary of freeware, and avoid pirated software or media. Pirated software carries a greater risk of adware and other types of malware.
- Read end-user software license agreements before downloading free software to find out if the app developers conduct information gathering through their program.
- Use a pop-up ad blocker to prevent unexpected windows from opening.
- Avoid clicking on ads if they are not being displayed on a trusted site.
- Install and use antivirus software to detect and remove unwanted software.
Learn some best practices to prevent spyware infection and ways to remove it if infected.







