watering hole attack
What is a watering hole attack?
A watering hole attack is a security exploit in which the attacker seeks to compromise a specific group of end users by infecting websites that members of the group are known to visit. The goal is to infect a targeted user's computer and gain access to the network at the target's workplace.
The term watering hole attack comes from hunting. Rather than tracking its prey over a long distance, the hunter instead determines where the prey is likely to go, most commonly to a body of water -- the watering hole -- and the hunter waits there. When the prey comes of its own will, often with its guard down, the hunter attacks.
The target victim can be an individual, an organization or a group of people. The attacker profiles its targets -- typically, employees of large enterprises, human rights organizations, religious groups or government offices -- to determine the type of websites they frequent. These are often messaging boards or general interest sites popular with the intended target.
While watering hole attacks are uncommon, they pose a considerable threat since they are difficult to detect and typically target highly secure organizations through their less security-conscious employees, business partners or connected vendors. And, because they may breach several layers of security, they can be extremely destructive.
Watering hole attacks -- a type of social engineering attack -- are also referred to as water-holing, a water hole attack or a strategically compromised website.
Read more here about social engineering and other types of attacks.
How does a watering hole attack work?
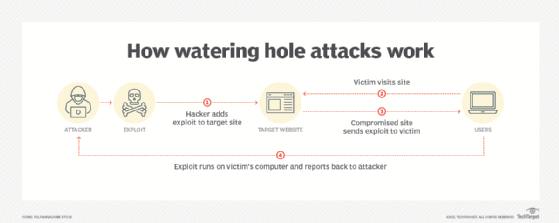
A watering hole attack involves a chain of events initiated by an attacker to gain access to a victim. However, the attacker does not target the victim directly.
First, the attacker identifies a website or service that the intended victim already uses and is familiar with. Generally, the target site has relatively low security, is frequently visited and is popular with the intended victim. The attacker then compromises the target site and injects a malicious code payload into the site, often in the form of JavaScript or HyperText Markup Language (HTML). When the victim visits the compromised site, the payload is triggered, and it begins an exploit chain to infect the victim's computer. The payload may be automatic, or the attack may cause a bogus prompt to appear telling the user to take an additional action that will download malicious code. The exploit chain may be one that already exists and is well known or a novel exploit created by the attacker.
Once the payload has been triggered on the victim's computer, the attacker can access other assets on the network and use that computer to launch a pivot attack to achieve other goals. The goals may be to gather information about the victim, use the victim's computer as part of a bot network or try to exploit other computers within the victim's network.
Other security exploits similar to watering hole attacks
A watering hole attack is similar to other tactics used by cybercriminals:
- Supply chain attack. In both a supply chain attack and a watering hole attack, a third-party service is compromised by the attacker to infect other systems. However, in supply chain attacks, it is usually a product purchased by the target that is compromised rather than the neutral websites compromised during a watering hole attack.
- Honeypot attack. A honeypot attack presents an attractive target that entices the victim to take an action, while a watering hole attack focuses on an existing site that the target already uses.
- Man-in-the-middle (MitM) attack. In a MitM attack, the attacker intercepts and reads or changes communication between the victim and a third-party site, but the site itself is not compromised.
- Tailgating. Tailgating is similar in that an attacker follows closely behind someone trusted to gain access, but it is most commonly a physical attack.
Read more here about how to build a honeypot to increase network security.
How to prevent a watering hole attack
These steps and operational requirements can help to avoid watering hole attacks:
- Use best practices for computer security. Since watering hole attacks are often web exploits, following published best practices and computer hardening guidelines may prevent the exploit chain from running.
- Do not allow personal use of corporate resources. Block access to websites not used for work, and do not allow users to access websites for personal communication.
- Do not add trusts to third-party sites. Some sites require additional permissions to run properly. Audit or simply don't allow these exceptions, as they may allow an attacker to use the site in the future.
- Train users to recognize strange behavior and avoid violations. Users may be lax with sites they commonly visit, so they should be trained to not click on suspicious links or bypass security warnings.
- Scan and monitor internet traffic. Use web proxies that can scan content in real time; monitor for common exploits; and use web logging to detect suspicious activity.
Examples of watering hole attacks
Watering hole attacks have been around for some time. Here are some notable examples of past attacks:
- In 2012, several sites were compromised, including the U.S. Council on Foreign Relations (CFR). The attack used the Gh0st Rat exploit and was known as the VOHO attacks.
- In 2016, the Canada-based International Civil Aviation Organization (ICAO) spread malware that infected the United Nations (UN) network.
- In 2017, Ukrainian government websites were compromised to spread the ExPetr malware.
- In 2019, many religious and humanitarian websites were compromised to target specific Asian communities.
Read more here about other types of security incidents and how to handle them.






