federated identity management (FIM)
What is federated identity management (FIM)?
Federated identity management (FIM) is an arrangement between multiple enterprises or domains that enables their users to use the same identification data (digital identity) to access all their networks. These partners are also known as trust domains. A trust domain can be an organization, a business unit, a smaller subsidiary of a larger organization, etc.
FIM is a system of single login, multiple access. For FIM to work effectively, all involved partners must have a sense of mutual trust. Each trust domain maintains its own identity management. However, all domains are interlinked through a third-party service that stores users' access credentials and provides the trust mechanism needed for FIM to work. This third service is known as the identity provider or identity broker.
This provider brokers access control among multiple service providers. The FIM arrangement is made between two -- or even more -- identity brokers across organizations.
FIM links users' identities across multiple security domains. When two domains are federated, users only need to authenticate themselves to one domain. That's because a second security domain -- and part of the FIM system -- trusts that the user's home domain authenticated the user and enables them to have unfettered access.
Examples of FIM systems include OpenID and Open Authorization, as well as Shibboleth, which is based on the Organization for the Advancement of Structured Information Standards' Security Assertion Markup Language (SAML).
How does federated identity management work?
FIM works because the FIM partners send each other Authorization messages. These messages can be transmitted using SAML or a similar Extensible Markup Language standard. Both enable users to log on once to access multiple affiliated but separate websites or networks.
Users' credentials are provided to and stored with their identity provider, which is their home domain. Then, when logging in to a service such as a software-as-a-service application, they don't have to provide credentials to the service provider. Rather, the service provider trusts the identity provider to validate these credentials and grant them access.
What are common federated identity management use cases?
FIM is useful when administering applications that need access to resources in multiple security domains.
Here are some common FIM use cases:
- new users added to the system after a merger or acquisition;
- external vendors or distributors that require access to the organization's resources;
- users from commercial identity providers;
- users with credentials from a public organization;
- citizens using credentials from a national identity provider; and
- access to social websites, like Gmail, Facebook, Google, etc.
What is the difference between SSO and FIM?
Single sign-on (SSO) is an important component of FIM, but it is not the same as FIM.
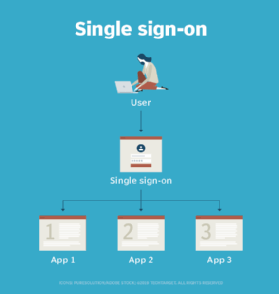
SSO enables users to use a single set of credentials to access multiple systems within a single organization. It is token-based, meaning that users are identified by a token rather than a password.
FIM enables users to access systems across federated organizations. They can use the same credentials to access the applications, programs and networks of all members within the federated group. It provides single-step access to multiple systems across different organizations. Unlike SSO, FIM users don't provide credentials directly to a web application, but to the FIM system itself.
Organizations that implement SSO do not necessarily use FIM. However, FIM relies heavily on SSO technologies to authenticate users across domains.
What are benefits and drawbacks of federated identity management?
When organizations work together on a project, FIM enables participants to access and share resources across all domains. FIM also simplifies the process of authenticating and authorizing users of the systems within the federation.
At the same time, administrators in each organization still control access levels in their own domains. They can set permissions and access levels across different systems in different security domains for a user based on a single username. This reduces their work and simplifies identity and access management.
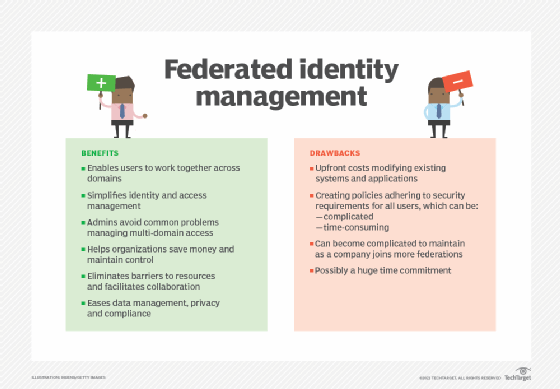
Administrators can also avoid common issues that crop up when balancing multi-domain access, such as developing a specific system to make it easy to access the resources of an external organization. The consolidation approach of FIM helps organizations save money and maintain control.
FIM also eliminates the barriers that often prevent users from easily and securely accessing the resources they need. It delivers convenience so they can securely access systems in different domains without having to remember multiple credentials or log in multiple times. Consequently, the user can save time, minimize access friction and increase productivity.
FIM also simplifies data management, privacy and compliance, and it reduces storage costs.
One drawback of FIM is the upfront costs that organizations incur to modify existing systems and applications. This can be a substantial financial burden for smaller organizations.
Another challenge is that participating federation members must create policies that adhere to the security requirements of all members. This negotiation can be a complicated, time-consuming undertaking when each enterprise sets different requirements and rules.
Finally, a participating organization can be a member of more than one federation, so its policies should reflect the rules and requirements of each federation. As the company joins additional federations, this can become complicated and require a huge time commitment that many enterprises may not be prepared for.







