email spam
What is email spam?
Email spam, also known as junk email, refers to unsolicited email messages, usually sent in bulk to a large list of recipients. Spam can be sent by real humans, but more often, it is sent by a botnet, which is a network of computers (bots or spambots) infected with malware and controlled by a single attacking party (bot herder). Apart from email, spam can also be distributed via text messages or social media.
Most people find spam annoying but consider it an inevitable side effect of using email communication. While spam is annoying -- it can choke email inboxes if not properly filtered and regularly deleted -- it can also be a threat.
Email spam senders, or spammers, regularly alter their methods and messages to trick potential victims into downloading malware, sharing data or sending money.
Spam emails are almost always commercial and driven by a financial motive. Spammers try to promote and sell questionable goods, make false claims and deceive recipients into believing something that's not true.
The most popular spam subjects include the following:
- pharmaceuticals
- adult content
- financial services
- online degrees
- work-from-home jobs
- online gambling
- cryptocurrencies
A common misconception is that spam is an acronym that stands for "stupid pointless annoying malware." The term is actually derived from a famous Monty Python Flying Circus sketch in which there are many repetitive mentions of the canned meat product Spam.
Spam, spammers and spambots
Spammers use spambots to crawl the internet looking for email addresses that are used to create email distribution lists. The lists are used to send junk email to multiple email addresses -- usually hundreds of thousands -- at one time.
The conversion rate for spam is low. Simply put, few people actually fall for emails from rich but desperate Nigerian princes or from so-called pharmaceutical businesses claiming to hold the patent on a miracle lose-weight-fast pill.
Spammers expect only a small number of recipients to respond or interact with their message, but they can still swindle their way to a big payday because they can easily send their shady message to so many emails addresses in a single stroke. That is why spam continues to be a big problem in the modern digital economy.

A brief history of spam
Spam might be a modern problem, but it has a history that goes back several decades. The first spam email was sent out in 1978 by Gary Thuerk, an employee of the now-defunct Digital Equipment Corp. (DEC), to promote a new product. The unsolicited email went out to about 400 of the 2,600 people who had email accounts on the Advanced Research Projects Agency Network. Some reports suggest that it generated about $12 million in new sales for DEC.
However, it wasn't until 1993 that the term spam was used. It was applied to Usenet, a newsgroup that's a hybrid between an email and web forum. A glitch in its new moderation software caused it to automatically post 200-plus messages to a discussion group. Someone jokingly called the event spamming.
Usenet was also the victim of the first large-scale spam attack in 1994. By 2003, spam constituted 80% to 85% of email messages sent worldwide. It had already become such a widespread problem that it prompted the U.S. to pass the Controlling the Assault of Non-Solicited Pornography and Marketing (CAN-SPAM) Act of 2003. CAN-SPAM is still the most important regulation that legitimate email marketers must comply with to prevent being labeled as spammers.
Between mid-2020 and early 2021, the average daily spam volume fell from 316.39 billion to about 122 billion. However, 85% of all emails are still spam, which costs legitimate businesses billions of dollars every year.
Common spamming techniques
Spammers use several different techniques to send spam, including the following:
- Botnets. Botnets enable spammers to use command-and-control servers to both harvest email addresses and distribute spam.
- Snowshoe spam. With this technique, spammers use a wide range of Internet Protocol (IP) addresses and email addresses with neutral reputations to distribute spam widely.
- Blank email spam. This technique involves sending email with an empty message body and subject line. It could be used in a directory harvest attack to validate email addresses by identifying invalid bounced addresses. In some instances, seemingly blank emails may hide viruses and worms that can spread through Hypertext Markup Language code embedded in the email.
- Image spam. The message text, which is computer-generated and unintelligible to human readers, is stored as a JPEG (Joint Photographic Experts Group) or GIF (Graphics Interchange Format) file and placed into the email body. This method attempts to avoid detection from text-based spam filters.
Types of spam
Email spam comes in many forms, depending on the purpose of the spammer, including the following:
- Marketing messages. This type of spam peddles unsolicited or illegal products or services.
- Malware messages. Some spam emails contain malware, which can trick users into divulging personal information, paying money or taking some action they would not normally do.
- Frauds and scams. The advance fee/Nigerian prince scam is a well-known example of email-based fraud. A user receives an email with an offer that purportedly results in a reward if they pay an advance fee or small deposit. Once they make the payment, the fraudster will invent further fees or just stop responding.
- Antivirus warnings. These messages "warn" a user about a virus infection and offer a "solution" to fix it. If the user takes the bait and clicks on a link in the email, the hacker can gain access to their system. The email may also download a malicious file to the device.
- Sweepstakes winners. Spammers send emails claiming that a recipient has won a sweepstakes or a prize. To collect the prize, the recipient must click on a link within the email. The link is malicious and is typically used to steal the user's personal information.
Spam may also come in the form of phishing emails.
Spam vs. phishing
Phishing messages are usually disguised as official communication from legitimate senders, like banks, online payment processors, government agencies or any other organization a user may trust.
These emails typically direct recipients to a fake version of a real organization's website, where the user is prompted to enter personal information, such as login credentials or credit card details -- information that can be used steal the victim's money or identity.
Phishing emails are more sophisticated than normal spam emails, which are usually mass-mailed, have a monetary focus and don't require the spammer to have a lot of technical expertise.
Antispam laws
Apart from the CAN-SPAM legislation in the U.S., other countries and political entities have also implemented laws to fight the spam menace, including the following:
- Australia: Spam Act 2003
- United Kingdom: Privacy and Electronic Communications Regulations
- Canada: Canada antispam legislation
- European Union: Privacy and Electronic Communications Directive 2002
How to fight spam
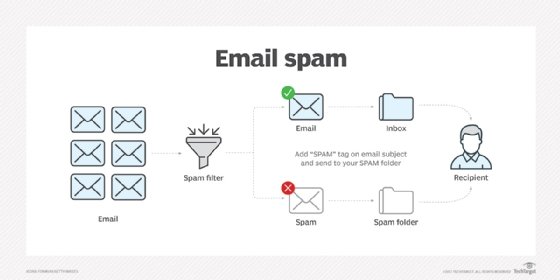
Email spam filters, which may be part of a security application or an email system add-on, can catch many spam messages, depositing them in a user's spam folder rather than their inbox. However, it's impossible to completely eliminate spam. Some newer filters can read images and locate the text in them, but that may inadvertently filter out nonspam emails that contain images featuring text.
Nonetheless, users can reduce their vulnerability to spam emails via the following:
- reporting, blocking and deleting instances of spam messages -- or any suspicious-looking messages -- that appear in their inboxes;
- adding a third-party antispam filter on local email clients;
- customizing the filter to block messages that include particular words or phrases that appear frequently in spam emails;
- creating an email allowlist of the specific email addresses, IP addresses or domains the user trusts and is willing to receive email from;
- using a disposable email account or masked email address for online use, e.g., in forums; and
- never clicking on links or opening attachments in emails from unknown senders.
Legitimate senders can stop their emails from being mistaken as spam by doing the following:
- maintaining their sender reputation;
- using authentication instruments, like DomainKeys Identified Mail and Sender Policy Framework;
- removing words that might be flagged by antispam filters and lead to the email being marked as spam;
- creating relevant, user-friendly content;
- optimizing email deliverability with good subject lines;
- asking users to opt in to ensure that they are engaged and less likely to mark the email as spam; and
- using a reliable bulk email service.






